Updated on January 12, 2026, by OpenEDR
Web applications are the backbone of modern businesses—but are they truly secure? From online banking to SaaS platforms and eCommerce portals, attackers increasingly target web apps as their primary entry point. This is where WAF information security becomes a critical layer of defense.
In today’s evolving threat landscape, traditional perimeter security is no longer enough. Organizations need intelligent, adaptive protection that can identify and block malicious traffic in real time. WAF information security plays a vital role in protecting sensitive data, maintaining uptime, and ensuring regulatory compliance.
This guide breaks down everything IT managers, cybersecurity professionals, and business leaders need to know about WAFs—how they work, why they matter, and how to deploy them effectively.
What Is WAF Information Security?
WAF information security refers to the use of a Web Application Firewall (WAF) to protect web applications from common and advanced cyber threats. A WAF sits between users and web applications, inspecting HTTP/HTTPS traffic to identify and block malicious activity.
Unlike traditional firewalls that focus on network-level threats, WAFs operate at the application layer (Layer 7). This allows them to understand user behavior, application logic, and attack patterns that network firewalls often miss.
Key Functions of WAF Information Security
Filters malicious web traffic
Prevents exploitation of application vulnerabilities
Blocks known and unknown attack patterns
Ensures application availability and data integrity
By strengthening WAF information security, organizations reduce the risk of data breaches, downtime, and reputational damage.
Why WAF Information Security Is Critical in 2026
Cyberattacks are becoming more frequent, automated, and sophisticated. According to industry reports, web application attacks account for over 40% of all data breaches globally.
Here’s why WAF information security is now a necessity—not a luxury:
1. Expanding Attack Surface
Cloud adoption, APIs, microservices, and remote work environments have expanded the attack surface dramatically.
2. Rise in Zero-Day Exploits
Attackers increasingly use zero-day vulnerabilities that bypass traditional security tools.
3. Compliance and Regulatory Pressure
Standards like PCI DSS, HIPAA, GDPR, and ISO 27001 require strong web application protection.
4. Business Continuity Risks
Downtime caused by attacks such as DDoS can cost organizations millions in lost revenue.
Strong WAF information security mitigates these risks by providing continuous, intelligent protection.
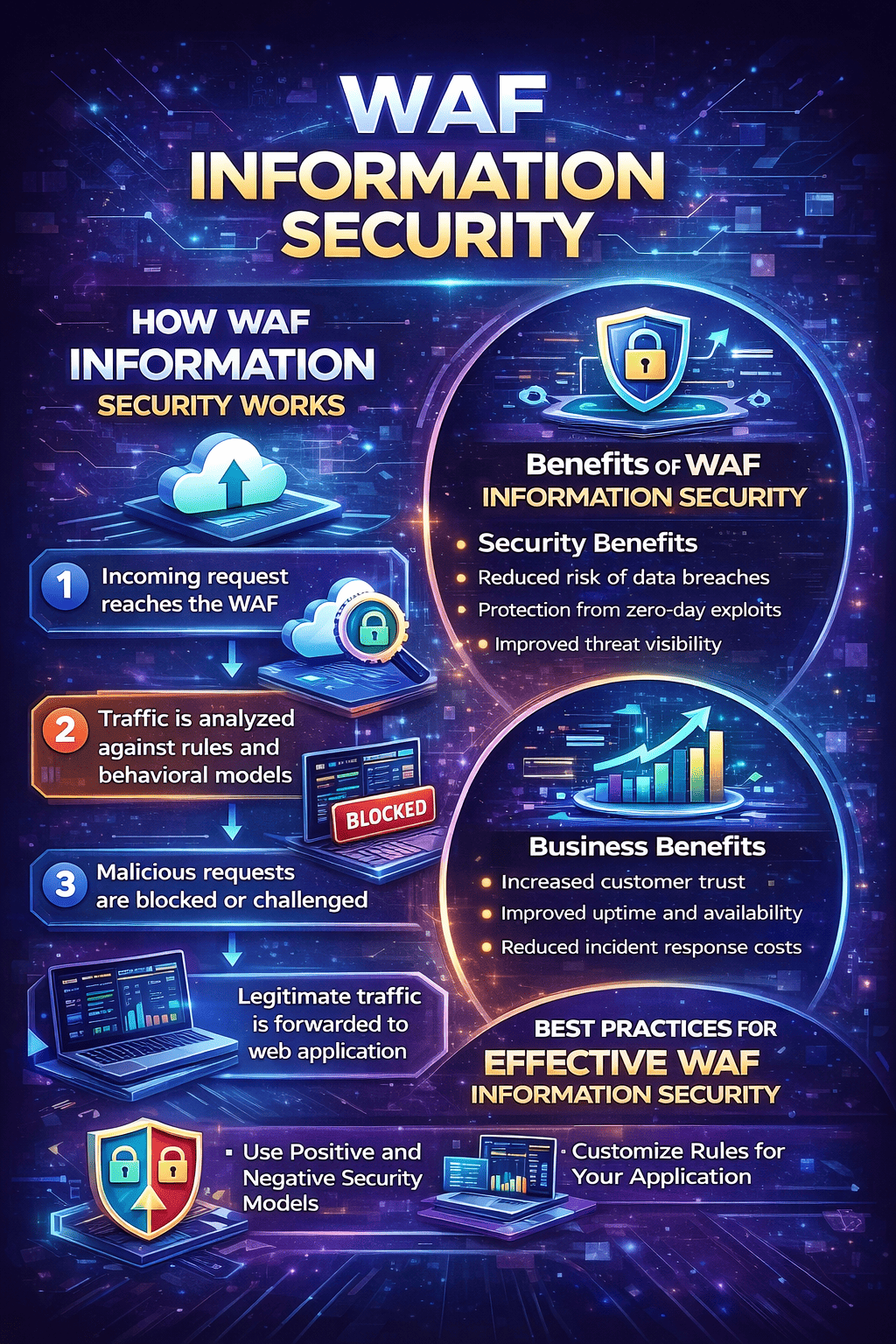
How WAF Information Security Works
At its core, WAF information security works by analyzing web traffic in real time and applying predefined or adaptive security rules.
Traffic Inspection Process
Incoming request reaches the WAF
Traffic is analyzed against rules and behavioral models
Malicious requests are blocked or challenged
Legitimate traffic is forwarded to the web application
Detection Methods Used in WAFs
Signature-based detection – Matches known attack patterns
Behavioral analysis – Detects abnormal user behavior
Rate limiting – Prevents brute-force and DDoS attacks
Machine learning – Adapts to evolving threats
Modern WAF information security solutions use AI-driven analytics to improve accuracy and reduce false positives.
Common Threats Prevented by WAF Information Security
A properly configured WAF protects against the most dangerous web-based attacks.
OWASP Top 10 Threats
SQL Injection (SQLi)
Cross-Site Scripting (XSS)
Cross-Site Request Forgery (CSRF)
Remote Code Execution
Broken Authentication
Additional Threats Blocked
Bot attacks and credential stuffing
DDoS attacks
API abuse
File inclusion attacks
By addressing these threats, WAF information security acts as a frontline defense for modern applications.
Types of WAF Information Security Solutions
Choosing the right WAF depends on business size, infrastructure, and security needs.
1. Network-Based WAF
Deployed on-premises
Low latency
Higher maintenance costs
2. Host-Based WAF
Integrated into application servers
Highly customizable
Requires development expertise
3. Cloud-Based WAF (Most Popular)
Easy to deploy and scale
Ideal for cloud and hybrid environments
Managed and continuously updated
Cloud-native WAF information security solutions are preferred by enterprises due to flexibility and lower operational overhead.
Benefits of Implementing WAF Information Security
Implementing a strong WAF delivers measurable security and business benefits.
Security Benefits
Reduced risk of data breaches
Protection from zero-day exploits
Improved threat visibility
Business Benefits
Increased customer trust
Improved uptime and availability
Reduced incident response costs
Compliance Benefits
Supports PCI DSS, HIPAA, and GDPR requirements
Helps meet audit and reporting standards
When aligned correctly, WAF information security becomes a strategic business enabler—not just a security tool.
Best Practices for Effective WAF Information Security
To maximize protection, organizations must go beyond basic deployment.
1. Use Positive and Negative Security Models
Allow known-good traffic while blocking suspicious behavior.
2. Customize Rules for Your Application
Generic rules are helpful, but application-specific tuning improves accuracy.
3. Monitor and Update Continuously
Threats evolve daily. Continuous monitoring is essential.
4. Integrate with SIEM and SOC Tools
Centralized visibility improves response times.
5. Combine WAF with Endpoint and Zero Trust
WAF information security works best as part of a layered security approach.
WAF Information Security vs Traditional Firewalls
| Feature | Traditional Firewall | WAF Information Security |
|---|---|---|
| Protection Level | Network layer | Application layer |
| Threat Awareness | Limited | Deep application context |
| OWASP Protection | ❌ | ✅ |
| API Security | ❌ | ✅ |
| Zero-Day Defense | ❌ | ✅ |
This comparison highlights why WAF information security is essential for modern application protection.
Who Needs WAF Information Security?
WAF protection is no longer limited to large enterprises.
Ideal for:
IT Managers securing internal and customer-facing apps
CISOs managing enterprise risk
CEOs and Founders protecting brand reputation
SaaS providers and cloud-native businesses
Financial, healthcare, retail, and government sectors
If your organization relies on web applications, WAF information security is non-negotiable.
Future of WAF Information Security
The future of WAFs is intelligent, automated, and cloud-native.
Emerging Trends
AI-driven threat detection
Zero Trust integration
API-first security models
Autonomous remediation
As cyber threats evolve, WAF information security will continue to adapt—becoming smarter and more proactive.
Frequently Asked Questions (FAQ)
1. What is WAF information security used for?
WAF information security protects web applications by filtering malicious HTTP/HTTPS traffic and preventing common web-based attacks.
2. Is WAF information security necessary for small businesses?
Yes. Small businesses are frequent attack targets due to weaker defenses. A cloud-based WAF offers affordable, scalable protection.
3. Can a WAF stop zero-day attacks?
Modern WAFs use behavioral analysis and machine learning to detect and block zero-day threats in real time.
4. Does WAF information security impact website performance?
When properly configured, a WAF improves performance by filtering malicious traffic and reducing server load.
5. How does WAF support compliance?
WAF information security helps meet PCI DSS, GDPR, and HIPAA requirements by protecting sensitive data and preventing breaches.
Final Thoughts: Strengthen Your Security with WAF Information Security
Cyber threats will only continue to grow in scale and sophistication. Relying on outdated security measures puts your business at risk. WAF information security provides the intelligent, adaptive protection needed to safeguard modern web applications.
If you’re ready to take a proactive step toward stronger application security, now is the time.
👉 Protect your web applications today. Get started here:
https://openedr.platform.xcitium.com/register/