A comprehensive guide to the best practices for How to deploy XDR platform
Updated on April 6, 2023, by OpenEDR
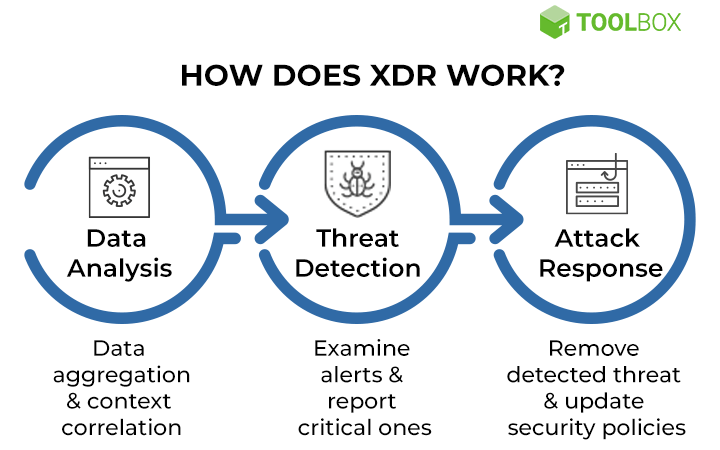

How to deploy XDR work?
XDR stands for Extended Detection and Response, a combined security solution of Endpoint Detection and Response, Network Detection and Response, and Security Information and Event Management capabilities. All these security components enable it to give a comprehensive view of an organization’s security posture. These components offer a more holistic and efficient security approach to organizations.
XDR Explained: XDR works on creating a unique attack story with advanced analytics and machine learning techniques. It combines data from endpoints, networks, cloud environments, and other relevant sources. It detects and responds to threats across the organization’s infrastructure using machine learning algorithms and advanced analytics.
For instance, a company is using XDR platform to protect its infrastructure. It can easily detect a malware infection provided on a single endpoint and automatically trigger a response for isolating the infected device. Then it would investigate the attack and provide a remedy for that issue. You should know how to deploy XDR to detect and correlate threat indicators across multiple endpoints and networks and respond to sophisticated threats that evade traditional security solutions.
Assessing XDR platforms
Most commercially available XDR platforms use similar architectures and processes. But there are some distinct features you should know about before purchasing the XDR SaaS-based security tool. It is usually considered the evolution of EDR into a primary incident response tool.
XDR Tools:
OpenEDR®, the best XDR security solution provider can avail of analytic detection with Mitre ATT&CK visibility for learning adversarial threat activity and behaviors in real-time for your XDR operations regardless of the size of the cybercriminals.
Various factors depend on choosing the XDR product that best fits your organization’s needs. Here are the purchase decision aspects to consider:
- Upto which extent are users distributed geographically
- Where do you keep your applications, data and servers like on-premise, or could sources
- Your sensitive data passes over unreliable networks or servers like the internet.
- Consider a reliable XDR vendor to proactively handle threat intelligence and detect data threats
- AI capabilities are integrated into the best XDR platform for effective threat detection and overall reduction of false positives.
How to Deploy XDR Platform – XDR Security Solutions Deployment Tips
- Developing security strategy
Before planning an XDR rollout, quantify how much will be collected and how long it will be stored. Developing a comprehensive security strategy is key to knowing how to deploy XDR. This would help the organization identify potential risks and vulnerabilities. Make sure to evaluate existing security solutions and define your security objectives. The XDR strategy should include incident response plans and protocols, establishing clear lines of communication and responsibility in the organization.
- Select the best XDR solution
It’s essential to choose the best XDR solution before you get on with how to deploy XDR successfully. The XDR solution should offer comprehensive coverage across multiple vector line endpoints, networks, cloud and applications. It should be easy to use and manage with features like automated threat detection and response, easy-to-understand analytics, real-time alerts, etc.
- Conduct thorough testing and evaluation
While conducting tasks for deploying XDR in your organization, ensure thorough testing and evaluation to evaluate if the solution is effective and compatible with your existing security infrastructure. The testing process for how to deploy XDR may involve pilot testing and evaluating concept and performance metrics for response times, detection rates and false positives.
- Proper integration of existing security solutions
The vendor you are working with should give you a detailed guide on how to deploy XDR solution. It should be integrated seamlessly with your existing security solutions to ensure maximum effectiveness. The XDR platform should communicate with other security solutions like EDR, SIEM, and firewalls, and the data and alerts should be shared across different platforms. While conducting how to deploy XDR practice, coordinate well with the IT and security teams.
- Use automated patching
Implement automated patching across all endpoint devices with updated or latest security patches. Your organization can use various tools for the automated patching process of how to deploy XDR, like patch management systems. Your vendor can offer a central console for viewing and deploying patches. Moreover, implement a phased rollout approach to avoid any failure. It would ensure the integration does not affect the business operations. Use ongoing services for improvement over time.
Conclusion: How to Deploy XDR
If deployed properly, XDR platform can be a powerful tool in your organization to fight against cyber threats and offer you appropriate remedies. Follow the aforementioned deployment tips with careful planning and execution to maximize the effectiveness of your security solutions and protect against evolving cyber attack behaviors.
FAQ Section