EDR Vs Antivirus – What Endpoint Security Solution You Need?
Updated on March 2, 2023, by OpenEDR
EDR Vs Antivirus
Endpoint attacks are becoming quite common, and their security has become the biggest challenge for businesses. Cyber security experts are looking into different endpoint security solutions such as EDR, XDR, Antivirus, etc.
EDR Beyond Legacy Antivirus
Since using all these solutions is impossible, it’s important to compare available options and select the right choice. Let’s dive into EDR Vs Antivirus analysis and determine whether you need both options and whether one can replace another.
EDR Vs Antivirus- Get a Complete Understanding of Both Options
Before I compare both options, it’s good to understand these tools clearly.
What is EDR?
it stands for Endpoint Detection and Response System. It is designed to identify, prevent, and respond to known and unknown threats. Once you install an agent in your network, it continuously monitors all the endpoints’ activities and data. If it detects any malicious activity, it will send a security alert to IT Admin. Besides, this software quarantine infected endpoints and automatically responds to threat.
What is Antivirus?
Antivirus is a tool designed to scan files in operating systems to detect and stop known threats such as malware, trojans, worms, and viruses.
EDR Vs Antivirus: What is the Difference between EDR and Antivirus
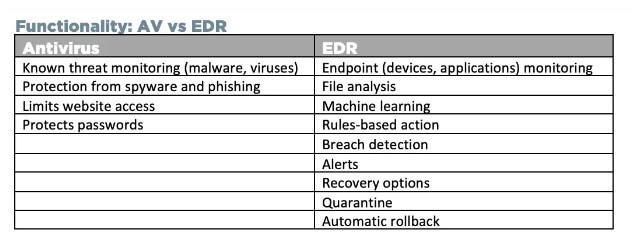
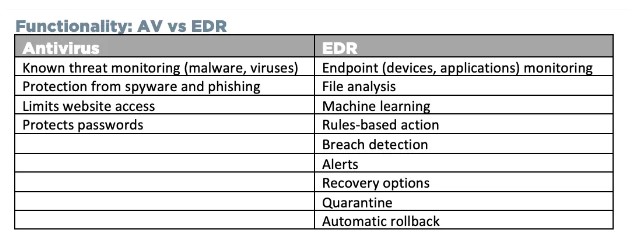
Here are the main differences between both endpoint security solutions.Basic Vs Advanced Technology
An antivirus solution relies on heuristic and signature-based detection technologies. You can find basic technologies in advanced-level Endpoint security solutions such as OpenEDR®.
Signature-based detection is essential in dealing with known threats.
Antivirus scans files and compares the code of new files with an existing database so that if any code matches a known threat, it can readily block and stop the threats.
The endpoint security agent is an advanced technology software with heuristic and detection-based technology to deal with known threats. But it goes beyond that technology. Many advanced Endpoint protection solutions are integrated with machine learning, behavior analysis, and artificial intelligence tool.
Limited Vs. Extended Protection
An antivirus can scan files and offer limited protection because it’s suitable for dealing with only already discovered threats. But today, your organization is exposed to brand new malware and threats. You must invest in comprehensive protection, which you can only get with an Endpoint protection tool.
Reactive Vs. Proactive Security Approach
Antivirus has a reactive security approach. It means that this tool will only act when a threat is there. It reacts to an attack or threat. EDR, on the other hand, is based on a proactive security approach. It can stop the threat and also prevent it.
Forensic and threat intelligence are the two main capabilities of an endpoint detection and response system. Your team can look into threats and attack through this tool. For example, an attack happens on an endpoint. Since you have security software, it readily stops this attack from spreading network-wide.
Once attack handling is done, the next phase would be to prevent similar attacks. An AV won’t be able to help you in this regard because Forensics needs to be included. However, endpoint protection software can help you in this regard.
Security analysts can run queries on the existing endpoint database or telemetry data. A thorough investigation makes it easy for your team to understand how this attack happened and what endpoints are vulnerable. Once you have this info, you can patch vulnerabilities.
Filed vs. Filed-less Attacks
Today, threat actors employ brand-new techniques, tactics, and procedures. They no longer plan file-based attacks. They are two steps ahead of cyber defense and plan fileless attacks. AV is good for dealing with file-based attacks, but it eventually fails when they are file-less. However, when you have an EDR, it tackles both kinds of attack well.
Does EDR Replace Antivirus Endpoint Protection?
If you get an advanced EDR containing next-generation antivirus capabilities, you can replace your antivirus with this endpoint security tool. However, it would be best if you opted for both solutions when your EDR doesn’t have such capabilities. It always depends on what you already have. If you don’t rely on an anti-malware program, it’s better to get modern
EDR solutions as they offer comprehensive coverage than a legacy AV.
EDR Vs Antivirus: Which One is the Right Choice?
An endpoint protection tool is always a better choice than an antivirus. It empowers your team to extend protection against known or unknown threats. All endpoints data and activities become visible to your team, and they can use filters to extract the data they need for threat investigation and Forensics.
Endpoint Security VS Antivirus Endpoint Protection: Cybercriminals know how to bypass legacy systems such as firewalls and antivirus. They can quickly pass this first line of defense. Thereby, you need an extra security layer, as in OpenEDR®. Even when malware gets past your anti-malware program, this threat won’t spread into your network because the endpoint agent will readily detect and stop it.
FAQ Section