EDR vs XDR: What’s the Point of Similarities and Difference?
Updated on March 2, 2023, by OpenEDR

Cyberattacks happen every 11 seconds around the globe. It’s no surprise that cybersecurity professionals are looking into the best solution that helps them protect digital assets.
EDR vs XDR
The most common solutions available in the market are Endpoint Detection Tools and Extended Detection& Response. Since it’s impossible to get it all, there is a need to understand EDR vs XDR completely. Let’s continue reading and get complete details about both cybersecurity solutions.
What is EDR?
It offers an integrated, layered approach to endpoint security. This software monitors and collects endpoint data for in-depth analysis while offering automated responses based on pre-set rules and criteria.
Endpoint attacks are widespread, making cyber criminals their favorite gateway to the overall organizational network. With the increasing trend of remote workers, it becomes easy for hackers to get unauthorized access to employee IDs and passwords and then crack the code of the entire business network.

How Does EDR Work?
Go through the below guide to learn how EDR works,
When it comes to protecting endpoints, OpenEDR® offers excellent security against ransomware, Trojans, and other types of malware.
Hackers made more than 700 million ransomware attack attempts in 2021.
Your organization can reduce the cost of a breach like ransomware through an Endpoint detection and response tool. It continuously monitors endpoints for malicious activities. If the software finds any anomaly on endpoints, it contains the threat and alerts the system administrator. Criminals won’t be able to access your whole system as their attack is analyzed in a sandbox or isolated environment.
What is XDR?
It is an extended detection and response system that provides comprehensive security on endpoints, networks, and cloud stations. This software is installed on your business network, collects data from multiple security layers, and correlates it. Your security team can detect threats fast as they get complete visibility into the entire IT Infrastructure of your organization. Besides, this tool improves their response time with better visibility and investigation techniques.
How Does XDR Work?
Go through the below guide to learn how to deploy XDR;
Security analysis needs to deal with alerts from different software. They feel overwhelmed with too many false positive investigations, especially with disconnected attack viewpoints.
This security challenge has always overcome these challenges. Once you have this tool, no cybercriminal will hide between security silo or disconnected network triage. Your SOC team will be equipped with a powerful tool, that lets them perform a detailed investigation into any behavioral activity or even on email, server, cloud workloads, networks, and endpoints,
The team can investigate faster without wasting time on manual tasks thanks to automatic XDR analysis. It offers a holistic approach for detection and response throughout your IT infrastructure, and it’s how you can improve your security posture.
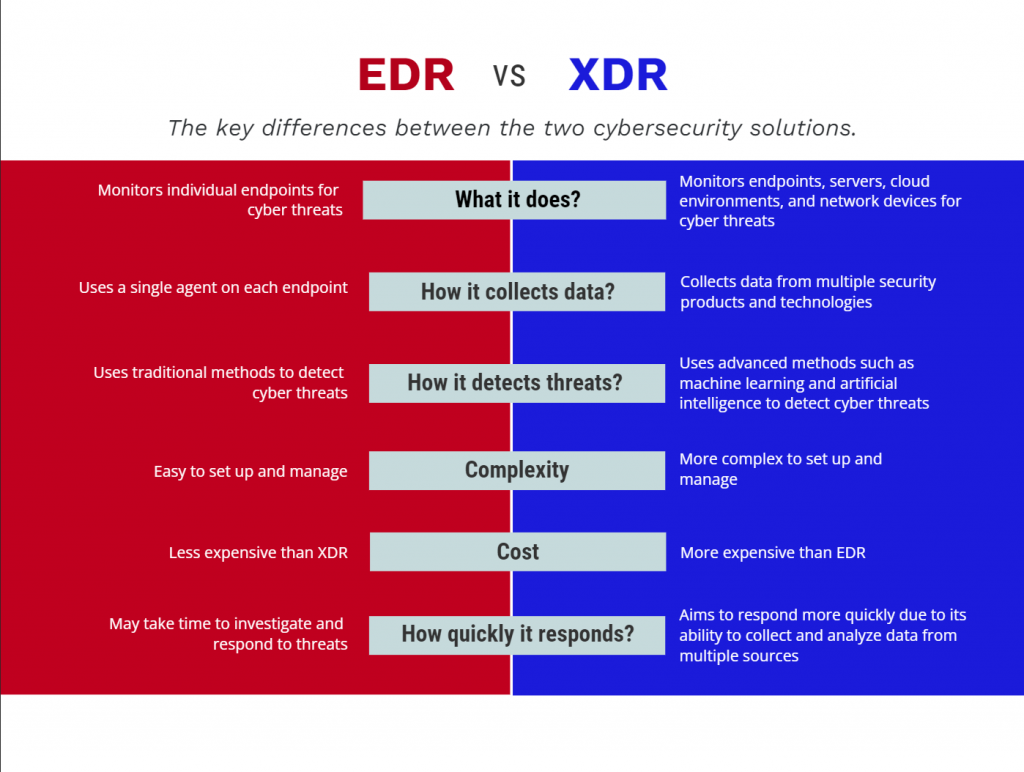
EDR vs XDR- What’s Similar?
You have got a clear idea of both tools and how they work. Now it’s time to know EDR vs XDR similarities. Here are similar functionalities of both tools.
- Preventative Approach: You need a security tool that helps you prevent and stop attacks and incidents. Thankfully, both EDR and XDR solutions are pretty helpful. They collect data and then apply data analytics and threat intelligence so that your team knows where the potential threat lies. It’s easy to prevent a threat before it spreads.
- Rapid Threat Response: Both solutions offer threat detection and response automation, which is a big plus. You can minimize the impact of an attack and avoid significant damage through them. For example, OpenEDR® contains malicious files in the containment system, so your team can analyze them. An attack on any network or endpoint won’t spread around as a result.
- Threat Hunting Support: Today, organizations deal with clever hackers and threat actors. They know how to bypass legacy systems and antivirus. There is a need to think beyond reactive security.
So, a quick EDR vs XDR analysis lets you understand these tools’ similar functionality; they are proactive security measures. Regardless of what device you get, it offers deep visibility and access to data, so your team can hunt threats proactively.
EDR vs XDR: What’s the Difference Between EDR and XDR
You already know what’s common between XDR and EDR. Now let’s understand their differences.
EDR only collects data from endpoints, while XDR collects data from the entire IT infrastructure, such as endpoints, workstations, cloud, and networks. Endpoint security is crucial as most cybercriminals attack your organization from this point, but it doesn’t mean you need to overlook other security areas. So, when looking for comprehensive coverage, you can opt for the Xtended Detection and Response Tool.
Wrap up – EDR vs XDR
Finally, you have to get a comparative analysis of EDR vs XDR. The question is, what solution does your organization need? It’s good to get dedicated endpoint security with an EDR, but extended protection with XDR makes more sense when securing all the aspects of your enterprises.
See Also
What is XDR
EDR Vendors
EDR
Endpoint Detection and Response