What Is EDR, And How Does EDR Work?
Updated on April 7, 2023, by OpenEDR
What Is EDR?
Endpoint detection and response (EDR) is an integrated endpoint security system that combines continuous real-time monitoring and data gathering from endpoints with capabilities for automated analysis and response based on rules. It is also dubbed as endpoint threat detection and response (ETDR).
In order to help security teams swiftly identify and address threats, Anton Chuvakin of Gartner came up with the word to define new security technologies that detect and look into suspicious activity on hosts and endpoints.
An EDR security system’s main purposes are to:
- Observe and gather endpoint activity data that may hint at a threat.
- Examine this information to look out for any threat patterns.
- automatically remove or contain threats if they are recognized, and alert security staff
- Tools for forensics and analysis to look for unusual activity and investigate risks that have been identified
How does EDR work?, and what should you look for in it?
- Endpoint Visibility:
You can see adversary behaviors even as they try to enter your environment thanks to real-time visibility across all of your endpoints, and you can halt them right away.
- Threat Database:
Massive volumes of data must be gathered from endpoints and contextually enhanced for effective EDR so that it may be mined for attack indicators using a range of analytical approaches.
- Behavioral Protection:
Indications of compromise (IOCs) and signature-based methods alone cause “silent failure,” which opens the door for data breaches. Behavioral techniques that look for indications of attack (IOAs) are essential for effective endpoint detection and response because they let you know about a suspicious activity before a breach takes place.
- Insight and Intelligence:
A threat intelligence-integrated endpoint detection and response solution can give you insight and intelligence, such as specifics on the ascribed adversary who is assaulting you or other facts about the attack.
- Fast Response:
EDR that permits rapid and accurate incident response can thwart an attack before it develops into a breach and help your firm quickly resume operations.
- Cloud-based Solution:
Having a cloud-based solution is the only way to ensure that there will be no effect on endpoints while making sure that functionalities like search and investigation can be carried out precisely and in real time.
How Does EDR Work?
Modern Advanced Persistent Threats (APTs) allow threat actors to slip past defenses undetected. Initial access brokers frequently use common attack strategies, techniques, and procedures, which endpoint detection and response solutions protect against. These initial access brokers could be malicious scripts, contaminated attachments, file-less malware, stolen user credentials, etc.
An Endpoint Detection and Response Solutions solution monitors all ongoing and current activities at the endpoints. It offers extensive threat intelligence and visibility. It enables advanced threat detection and investigations with the assistance of incident data search, suspicious activity detection and containment, and threat hunting.
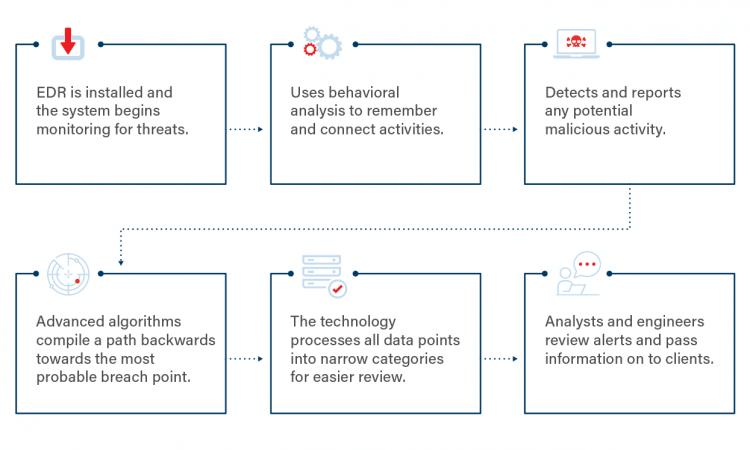
So, how does EDR work? The answer to the question is explained in the steps below.
How does EDR work? The answer is in its steps.
Systems that capture and archive endpoint-system-level activities are called endpoint detection and response (EDR) solutions. They employ various data analytics approaches to identify suspect system behavior, provide contextual data, stop malicious activity, and offer recommendations for corrective action to repair compromised systems.
How does EDR work? Step 1: Endpoint Data Monitoring
The conduction of endpoint monitoring and collection of data into a central database takes place here. Constant egress and ingress traffic monitoring at the endpoints permits an Endpoint Detection and Response solution. It helps to learn and decode safe and unsafe behavior attributes to intercept false positives and limit alert fatigue.
How does EDR work? Step 2: Anomaly Identification
An Endpoint Detection and Response solution swiftly identifies unknown behaviors at the endpoint. This offers organizations the cues to track an attacker’s path.
How does EDR work? Step 3: Automated Remediation
An Endpoint Detection and Response solution’s pre-configured rules can determine when incoming data points to a specific kind of security breach and initiates an automatic response, such as logging off the end-user or notifying a staff person. An Endpoint Detection and Response solution can automatically launch rapid incident response activities to stop indicators of compromise when configured with predetermined rules (IOCs).
How does EDR work? Step 4: Isolation of Affected Partitions
A detected cyber incident starts blocking impacted compartments, thwarting malicious artifacts from spreading across the network.
How does EDR work? Step 5: Investigation and Learning
An Endpoint Detection and Response solution isolates threats and automatically bars any IOCs upon detecting malicious activity. It then investigates the IOCs to thwart similar incidents in the future.
How does EDR work? Step 6: Alerting SOC Teams
After a breach, all affected data points are categorized and unified for further investigation and business continuity planning.
How does EDR work?: Get The Best EDR Solutions Here!
Check out the website below to get the best EDR solutions. Know more about your query by acquainting yourself with the website provided.
See Also:
How to Deploy EDR
FAQ Section