Updated on January 7, 2026, by OpenEDR
The modern enterprise no longer operates within a single network perimeter. Remote work, cloud adoption, and mobile users have redefined how organizations connect and operate. This shift has made SASE cybersecurity a critical strategy for protecting users, data, and applications—no matter where they are located.
Traditional security models struggle to keep up with today’s distributed environments. In contrast, SASE cybersecurity delivers security and networking as a unified, cloud-based service. This guide explains what SASE cybersecurity is, how it works, why it matters, and how organizations can adopt it successfully.
What Is SASE Cybersecurity?
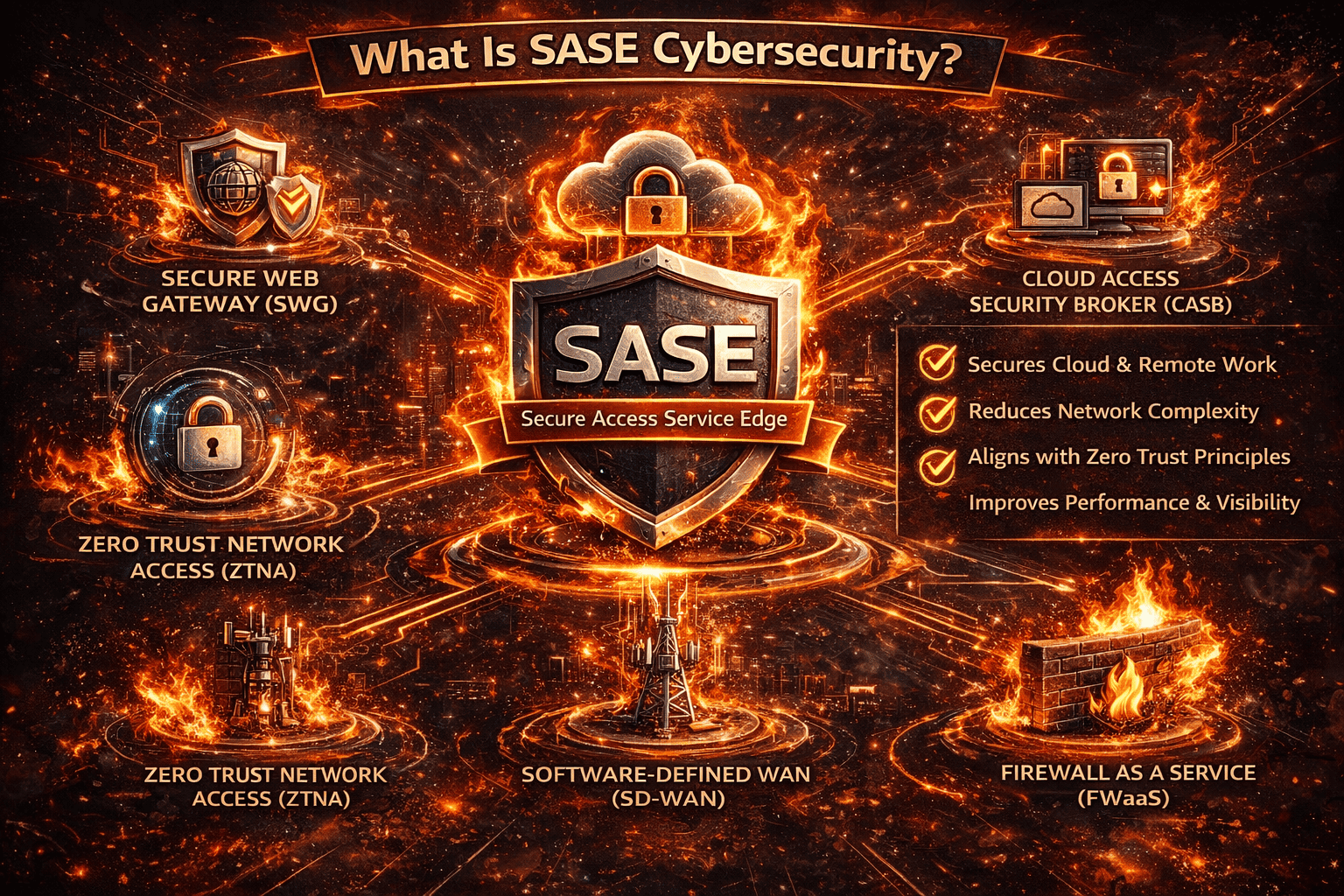
SASE cybersecurity stands for Secure Access Service Edge. It is a framework that combines network security and wide-area networking (WAN) capabilities into a single, cloud-delivered service.
Instead of routing traffic through centralized data centers, SASE cybersecurity applies security controls close to the user. This approach improves performance, visibility, and protection across cloud, remote, and on-prem environments.
SASE cybersecurity was introduced by Gartner to address the limitations of perimeter-based security in a cloud-first world.
Why SASE Cybersecurity Matters Today
The rise of remote work and SaaS applications has expanded the attack surface dramatically. Users now access corporate resources from anywhere, often using unmanaged devices and unsecured networks.
SASE cybersecurity matters because it:
Protects users regardless of location
Secures cloud and SaaS access
Reduces network complexity
Improves performance and user experience
Aligns with Zero Trust principles
For IT managers and business leaders, SASE cybersecurity is a response to modern operational realities.
Core Components of SASE Cybersecurity
To fully understand SASE cybersecurity, it’s important to break down its core components. These elements work together to provide end-to-end protection.
1. Secure Web Gateway (SWG)
Filters web traffic to block malicious websites, malware, and phishing attempts.
2. Cloud Access Security Broker (CASB)
Provides visibility and control over cloud applications and data usage.
3. Zero Trust Network Access (ZTNA)
Ensures users only access applications they are authorized to use—never the full network.
4. Firewall as a Service (FWaaS)
Delivers firewall protection through the cloud instead of on-prem hardware.
5. Software-Defined WAN (SD-WAN)
Optimizes traffic routing for performance and reliability.
Together, these components form the foundation of SASE cybersecurity.
How SASE Cybersecurity Works
SASE cybersecurity shifts security enforcement from centralized locations to cloud-based points of presence (PoPs). When a user connects to an application, traffic is routed through the nearest PoP.
Here’s how the process works:
A user attempts to access an application
Identity and device posture are verified
Security policies are applied in real time
Only authorized traffic is allowed
Continuous monitoring ensures compliance
This model delivers consistent security and performance across all environments.
SASE Cybersecurity vs Traditional Network Security
Traditional security models rely heavily on firewalls and VPNs tied to physical locations. SASE cybersecurity eliminates this dependency.
| Feature | Traditional Security | SASE Cybersecurity |
|---|---|---|
| Security Location | Data center-based | Cloud-delivered |
| User Access | Network-centric | Identity-centric |
| Scalability | Limited | Highly scalable |
| Performance | Often slow | Optimized |
| Remote Work | Complex | Built-in |
SASE cybersecurity is designed for distributed workforces and cloud-native operations.
Benefits of SASE Cybersecurity for Businesses
Organizations adopting SASE cybersecurity experience both security and operational benefits.
Key Benefits Include:
Reduced attack surface
Consistent security policies
Improved application performance
Simplified infrastructure
Lower operational costs
For CEOs and founders, SASE cybersecurity supports growth without increasing risk.
SASE Cybersecurity and Zero Trust
Zero Trust security assumes no user or device should be trusted by default. SASE cybersecurity aligns perfectly with this philosophy.
SASE enables Zero Trust by:
Verifying identity continuously
Enforcing least-privilege access
Monitoring behavior in real time
Preventing lateral movement
Together, Zero Trust and SASE cybersecurity create a resilient security framework.
SASE Cybersecurity for IT Managers
IT managers face increasing complexity managing security across cloud, remote, and hybrid environments. SASE cybersecurity simplifies this challenge.
SASE cybersecurity helps IT teams:
Centralize policy management
Reduce hardware dependencies
Improve visibility across users and apps
Automate security enforcement
Respond faster to threats
This centralized approach frees IT teams to focus on strategic initiatives.
SASE Cybersecurity for CEOs and Founders
From an executive perspective, SASE cybersecurity supports business agility and resilience.
Business leaders benefit from SASE cybersecurity by:
Reducing breach risks
Supporting remote and hybrid work
Improving customer trust
Enhancing compliance readiness
Enabling digital transformation
Security becomes a business enabler, not a bottleneck.
Common Use Cases for SASE Cybersecurity
SASE cybersecurity is especially valuable in modern, distributed environments.
Common Use Cases Include:
Securing remote workforces
Protecting SaaS and cloud apps
Replacing legacy VPNs
Enabling global branch connectivity
Supporting mergers and acquisitions
These use cases highlight the flexibility of SASE cybersecurity.
Challenges of Implementing SASE Cybersecurity
While powerful, SASE cybersecurity adoption requires careful planning.
Common Challenges:
Integrating legacy systems
Migrating from VPN-based access
Aligning teams around Zero Trust
Managing vendor consolidation
Training staff on new models
A phased approach helps organizations overcome these obstacles.
Best Practices for Adopting SASE Cybersecurity
Successful SASE cybersecurity deployment depends on strategy and execution.
Actionable Best Practices:
Assess current network and security gaps
Start with Zero Trust access controls
Prioritize cloud-native solutions
Simplify policies before migration
Monitor performance continuously
These steps reduce risk and accelerate value.
SASE Cybersecurity and Compliance
SASE cybersecurity supports compliance by enforcing consistent security controls and providing centralized logging.
It helps organizations meet requirements for:
Data protection regulations
Industry security standards
Access control mandates
Audit readiness
For regulated industries, SASE cybersecurity simplifies compliance management.
SASE Cybersecurity and Threat Prevention
Modern cyber threats are fast-moving and evasive. SASE cybersecurity improves prevention by inspecting traffic at the edge.
Key threat prevention capabilities include:
Real-time threat detection
Phishing and malware protection
Data loss prevention (DLP)
Continuous risk assessment
This proactive approach strengthens overall security posture.
The Future of SASE Cybersecurity
SASE cybersecurity continues to evolve alongside cloud and AI technologies.
Future trends include:
Deeper AI-driven threat detection
Greater automation of security policies
Enhanced user experience optimization
Tighter integration with endpoint security
Organizations investing in SASE cybersecurity today are preparing for tomorrow’s challenges.
Frequently Asked Questions (FAQs)
1. What is SASE cybersecurity in simple terms?
SASE cybersecurity is a cloud-based approach that combines networking and security into a single service.
2. Is SASE cybersecurity only for large enterprises?
No. Organizations of all sizes benefit, especially those with remote or cloud-first environments.
3. How is SASE different from a VPN?
SASE provides identity-based, application-level access, while VPNs grant broad network access.
4. Does SASE cybersecurity improve performance?
Yes. Traffic is routed through optimized cloud paths, reducing latency.
5. Is SASE cybersecurity secure?
Yes. When implemented correctly, it strengthens security through Zero Trust and continuous monitoring.
Final Thoughts: Why SASE Cybersecurity Is the Future
The traditional network perimeter no longer exists. Users, devices, and applications are everywhere—and security must follow. SASE cybersecurity provides a scalable, cloud-native approach that aligns security with how businesses actually operate today.
By adopting SASE cybersecurity, organizations gain stronger protection, better performance, and greater agility.
👉 Start your journey toward modern, unified security today:
Register now: https://openedr.platform.xcitium.com/register/