Updated on February 4, 2026, by OpenEDR
What if one stolen credential could shut down your entire business?
For many organizations today, that risk is very real. Cybercriminals no longer break in—they log in. And more often than not, they do it using privileged accounts.
This is where a PAM solution becomes not just helpful, but essential.
As cyberattacks grow more sophisticated and compliance pressures increase, organizations across industries are turning to Privileged Access Management to secure their most powerful accounts. In this guide, we’ll break down what a PAM solution is, why it matters, how it works, and how to choose the right one for your business.
What Is a PAM Solution?
A PAM solution (Privileged Access Management solution) is a cybersecurity framework designed to control, monitor, and secure access to privileged accounts. These accounts include administrators, root users, service accounts, and any identity with elevated permissions.
Unlike standard user accounts, privileged accounts can:
Modify systems and configurations
Access sensitive data
Disable security controls
Because of this, they are prime targets for attackers.
A modern PAM solution ensures that only the right users have the right level of access, for the right amount of time, and under strict monitoring.
Why Privileged Access Is a Major Security Risk
Privileged credentials are involved in a majority of serious cyber incidents. According to multiple breach reports, attackers often gain access by exploiting unmanaged admin accounts or stolen credentials.
Key risks of unmanaged privileged access:
Lateral movement across networks
Data exfiltration and ransomware deployment
Insider threats (malicious or accidental)
Regulatory non-compliance
Without a PAM solution, organizations often lack visibility into who is accessing critical systems—and why.
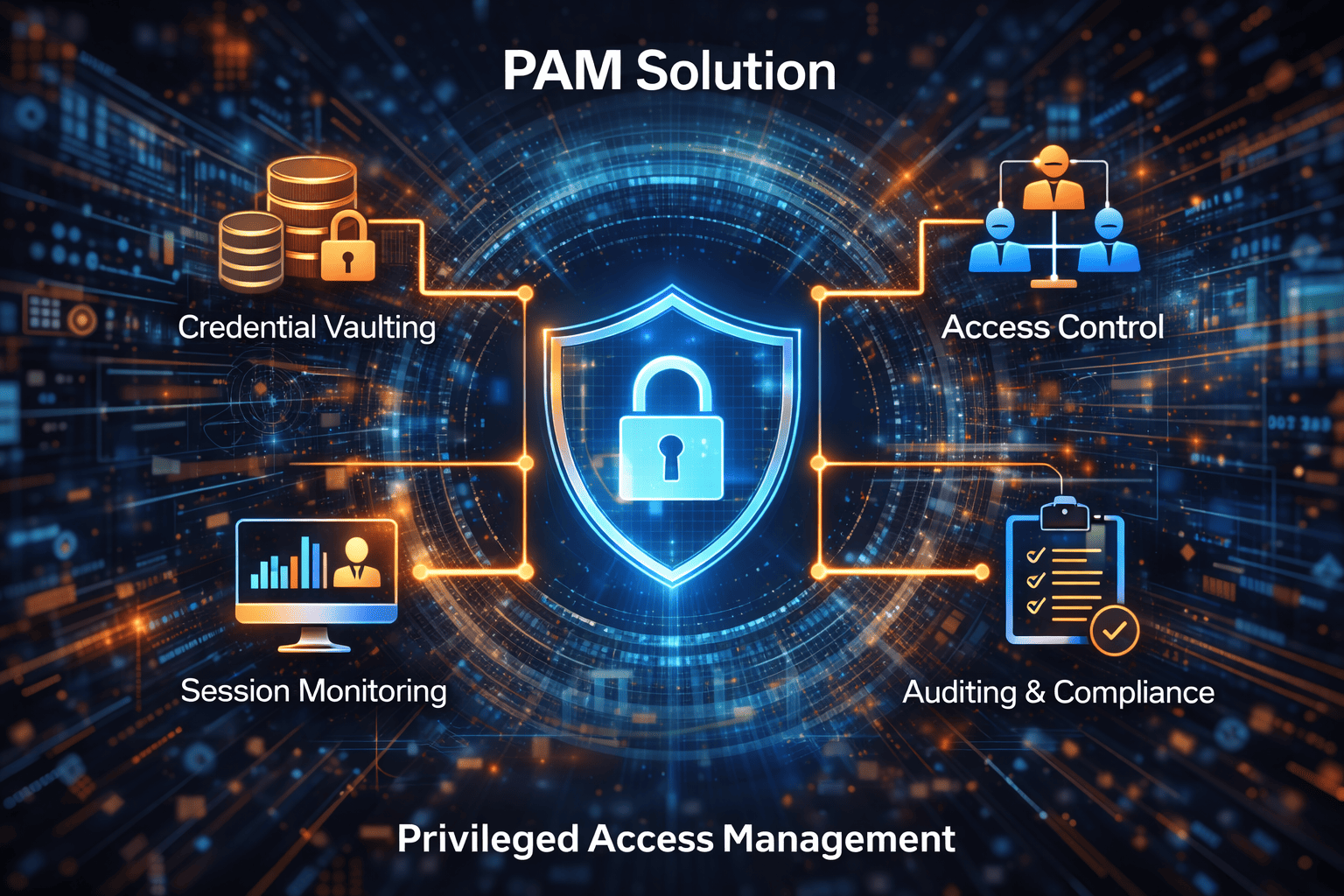
How a PAM Solution Works
A PAM solution operates by enforcing strict controls over privileged credentials and sessions. While implementations vary, most solutions include the following core mechanisms:
1. Credential Vaulting
Privileged passwords are stored in a secure, encrypted vault and rotated automatically.
2. Access Control & Least Privilege
Users receive only the permissions they need, reducing unnecessary exposure.
3. Session Monitoring & Recording
Privileged sessions are monitored in real time and recorded for auditing and forensic analysis.
4. Just-In-Time (JIT) Access
Access is granted temporarily and revoked automatically after use.
5. Audit & Compliance Reporting
Detailed logs ensure compliance with regulations like ISO 27001, SOC 2, HIPAA, and PCI DSS.
Together, these features make a PAM solution a cornerstone of Zero Trust security.
Key Features to Look for in a PAM Solution
Not all PAM platforms are created equal. When evaluating a PAM solution, look for these essential capabilities:
Core Features
Secure password vault
Automatic credential rotation
Role-based access control (RBAC)
Session recording and playback
Multi-factor authentication (MFA)
Advanced Capabilities
AI-driven anomaly detection
Cloud and hybrid environment support
Integration with SIEM and SOAR tools
API-based automation
Endpoint and DevOps privilege management
The best PAM solution balances strong security with operational efficiency.
PAM Solution vs Traditional Access Management
Many organizations mistakenly assume that IAM (Identity and Access Management) alone is enough. While IAM manages user identities, it does not adequately protect privileged accounts.
| Feature | IAM | PAM Solution |
|---|---|---|
| Standard user access | ✅ | ✅ |
| Privileged credential vaulting | ❌ | ✅ |
| Session recording | ❌ | ✅ |
| Just-in-time access | ❌ | ✅ |
| Admin activity monitoring | ❌ | ✅ |
A PAM solution complements IAM by securing the most powerful identities in your environment.
Benefits of Implementing a PAM Solution
Deploying a PAM solution delivers both immediate and long-term value.
Security Benefits
Reduced attack surface
Protection against credential theft
Prevention of insider threats
Faster incident response
Business Benefits
Improved regulatory compliance
Reduced operational risk
Enhanced visibility and control
Stronger trust with customers and partners
For executives and IT leaders, a PAM solution is not just a security tool—it’s a business enabler.
PAM Solutions Across Industries
Different industries face different privileged access challenges, but the need for a PAM solution is universal.
Healthcare
Protect patient records and meet HIPAA requirements.
Financial Services
Secure critical infrastructure and prevent fraud.
Manufacturing
Protect OT systems and intellectual property.
Technology & SaaS
Control DevOps access and cloud environments.
Government & Defense
Meet strict compliance and national security standards.
A flexible PAM solution adapts to each industry’s unique risk profile.
Cloud and Hybrid Environments: Why PAM Matters More Than Ever
As organizations migrate to cloud and hybrid infrastructures, privileged access expands dramatically. Cloud admins, service accounts, APIs, and containers all introduce new risks.
A cloud-ready PAM solution provides:
Unified visibility across environments
Secure access to cloud consoles
Protection for machine identities
Scalable privilege controls
Without PAM, cloud growth often leads to privilege sprawl, one of today’s biggest security blind spots.
Best Practices for Deploying a PAM Solution
To maximize the value of your PAM solution, follow these best practices:
Inventory all privileged accounts
Eliminate shared credentials
Enforce least privilege policies
Enable session monitoring
Integrate PAM with SIEM and SOC workflows
Continuously review and audit access
Successful PAM implementation is a journey, not a one-time project.
Common Challenges and How to Overcome Them
Resistance from IT Teams
Use automation and user-friendly workflows to reduce friction.
Complexity of Deployment
Choose a PAM solution with guided onboarding and strong vendor support.
Legacy Systems
Look for PAM platforms that support older protocols and environments.
The right PAM solution simplifies security instead of complicating it.
The Future of PAM Solutions
Modern PAM solutions are evolving rapidly. Key trends include:
AI-driven behavior analytics
Passwordless privileged access
Integration with Zero Trust frameworks
Unified identity security platforms
As attack surfaces grow, PAM will remain a non-negotiable pillar of cybersecurity strategy.
FAQs About PAM Solutions
1. What is a PAM solution used for?
A PAM solution is used to secure, monitor, and control access to privileged accounts that have elevated permissions within an organization.
2. Is a PAM solution necessary for small businesses?
Yes. Even small businesses are targeted by attackers, and privileged accounts remain a top attack vector regardless of company size.
3. How does a PAM solution improve compliance?
It provides audit trails, access logs, and controls required by standards like SOC 2, ISO 27001, HIPAA, and PCI DSS.
4. Can a PAM solution work in cloud environments?
Absolutely. Modern PAM solutions are designed for on-prem, cloud, and hybrid infrastructures.
5. How long does it take to deploy a PAM solution?
Deployment time varies, but many modern PAM platforms can be implemented in weeks—not months.
Final Thoughts: Why a PAM Solution Is No Longer Optional
Privileged access is the gateway to your most critical assets. Without proper controls, it becomes your biggest vulnerability.
A robust PAM solution helps organizations:
Stay ahead of attackers
Meet compliance requirements
Reduce operational risk
Build a stronger security posture
If you’re serious about protecting your business, customers, and reputation, now is the time to act.
Take the Next Step Toward Stronger Privileged Access Security
Ready to strengthen your security posture with a modern, intelligent approach to privileged access?
👉 Get started today:
https://openedr.platform.xcitium.com/register/
Your privileged accounts deserve enterprise-grade protection.