Updated on October 27, 2025, by OpenEDR
Have you ever asked yourself, what are fraud protection services and how they can shield your organization from rising cyber threats? In a world where global losses from online payment fraud surpassed USD $41 billion in 2022, according to one industry estimate, businesses cannot afford to be unprepared.
This blog post will unpack the concept of fraud protection services, examine the types of fraud they defend against, look at the core components of an effective service, and present clear tactics that IT managers, cybersecurity professionals, and business leaders can apply in their own operations.
1. Understanding Fraud Protection Services
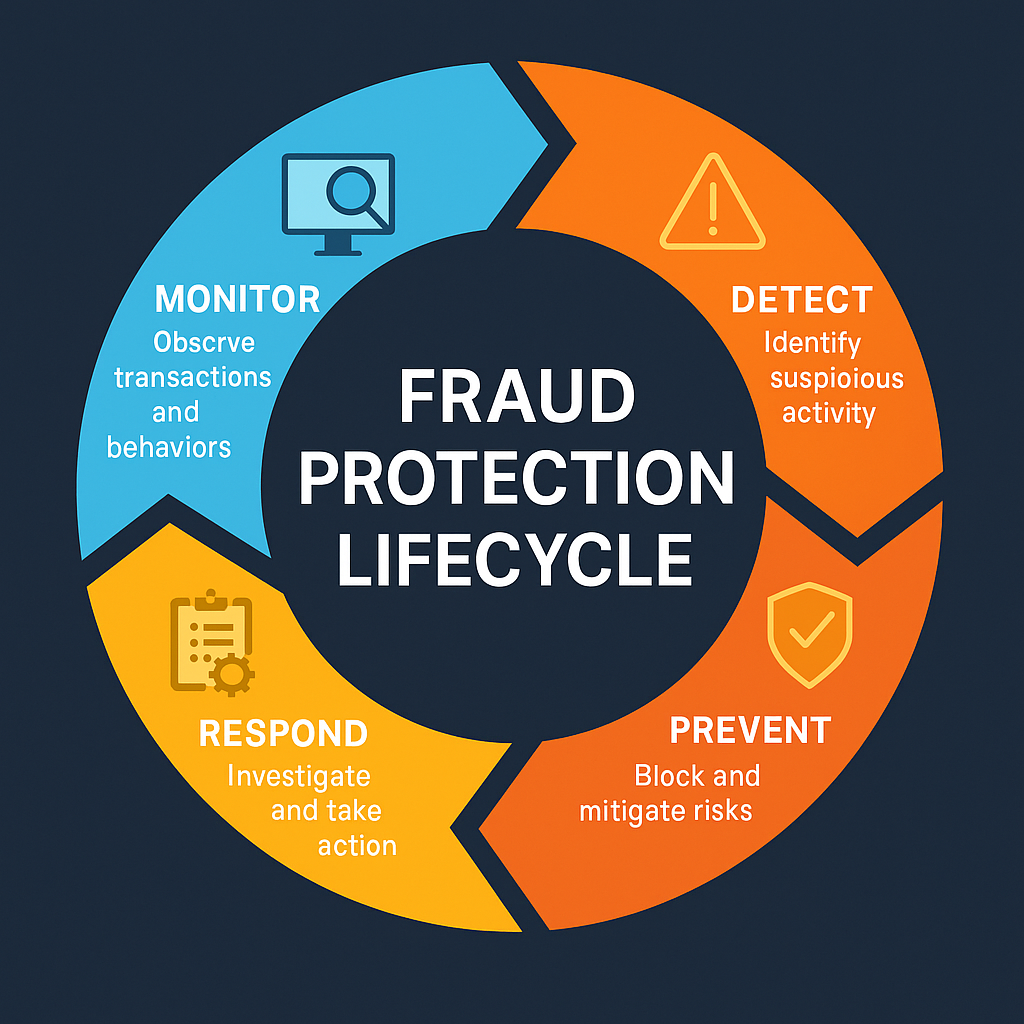
At its core, a fraud protection service is a managed offering—either by specialized vendors or internal teams—that helps organizations detect, prevent, and respond to fraudulent activity and financial crime.
These services combine advanced technologies (such as AI/ML models, behavioral analytics, and real-time monitoring) with operational workflows (alerts, investigation, and remediation). They’re relevant across industries: e-commerce, banking, insurance, supply chain and more.
Key Terms to Know
Fraud detection: Identifying suspicious patterns or transactions.
Fraud prevention: Stopping fraud before it happens (e.g., authentication, transaction rules).
Fraud response/remediation: Investigating incidents and recovering from them.
Chargeback/fraud loss mitigation: Minimizing financial loss and reputational damage.
2. Why Your Business Needs Fraud Protection Services
Fraud has grown more complex, blending digital channels with social engineering, identity theft, insider threat, and vendor collusion. For example:
Online payment fraud continues to surge worldwide.
Internal fraud (by employees) and B2B vendor fraud pose significant threats that many companies under-estimate.
Here are repercussions for not having adequate services:
Revenue loss from fraudulent transactions or chargebacks.
Regulatory fines (e.g., for money-laundering or privacy violations).
Reputational damage and customer trust erosion.
Operational disruption and increased investigation burden.
3. Types of Fraud Addressed by Services
A robust fraud protection service will cover multiple fraud types, including:
Payment & Transaction Fraud
Fraudulent credit-card transactions, account takeover, new-account fraud, money-laundering behaviours.
Identity Theft & Credential Fraud
Hackers obtaining real personal information (PII) to open accounts or masquerade as legitimate users.
Vendor and Supply-Chain Fraud
Fraudulent vendors, fake invoices, or compromised suppliers diverting money or goods.
Insider Fraud
Employees abusing access, manipulating payroll, committing fraud from inside the organization.
Check and ACH Fraud
Especially for businesses with high volume of payments: unauthorized debits or fake checks.
4. Core Components of Effective Fraud Protection Services
Below are the essential elements to look for in a fraud protection service:
Real-Time Transaction Monitoring
Systems analyse transactions immediately for anomalies (e.g., unusual location, high amounts, rapid successive purchases).
Authentication & Identity Verification
Multi-factor authentication (MFA), biometric verification, device fingerprinting and identity resolution help ensure the actor is who they claim to be.
Behavioral & Machine-Learning Models
These detect patterns that deviate from normal user or account behaviour, helping uncover emerging fraud trends.
Vendor & Third-Party Risk Management
Validating vendors, monitoring changes to vendor data, and preventing payment fraud within the supply chain.
Incident Response & Recovery
Once fraud is detected, the service should facilitate investigation, remediation, reporting and recovery—minimizing losses and protecting compliance.
Compliance and Reporting
Many services support compliance with regulatory frameworks (AML, KYC, PCI-DSS) and generate audit-friendly logs.
5. How to Choose the Right Fraud Protection Service
As an IT or security leader, selecting the right partner or solution requires careful evaluation. Consider these factors:
Tailored Industry Fit
Different industries face different fraud profiles—e-commerce sees payment fraud, manufacturing sees supply-chain fraud, finance sees layered money-laundering threats. A solution must align with your business.
Technology & Integration Capabilities
Look for AI-driven analytics, API integration, data enrichment, and compatibility with your existing systems (identity, payments, ERP, CRM).
Service Model: Self-Managed vs Managed
Some organizations have in-house capabilities; others need a fully managed provider that monitors, investigates and reports.
False-Positive Rate & Precision
High false-positives degrade experience and cost time. Services must balance risk sensitivity with accuracy.
Business Continuity & SLA Guarantees
Discuss response times, service level agreements, breach support and recovery procedures.
Cost vs ROI
Costs may include subscription fees, transaction-based pricing or outcome-based models. Compare against potential fraud loss, chargebacks, regulatory fines and reputational damage.
6. Implementing Fraud Protection Services in Your Organization
Here’s a practical roadmap to deployment:
Perform a Fraud Risk Assessment
Identify key fraud vectors and assets at risk (payments, vendors, credentials).
Quantify potential annual losses from different fraud types.
Define Monitoring Scope and Policies
Decide which transactions, vendors, accounts are monitored.
Set alert thresholds, approval rules and escalation workflows.
Select the Service Provider or Build In-House
Evaluate feature sets, integration, support and vendor track record.
Deploy & Integrate
Connect with payment gateways, ERP systems, user identity platforms.
Test with pilot segments and monitor outcomes.
Train Staff & Establish Response Protocols
Ensure fraud team knows how to review alerts, investigate, escalate and remediate.
Continuous Review & Optimization
Fraud evolves. Regularly tune models, update policies and evaluate new threat patterns.
7. Case Study: How One Business Stopped Paying Vendor Fraud
A manufacturing firm was losing thousands monthly due to false vendor invoices. By deploying a fraud protection service that validated vendor information in real time and cross-checked payments against historical patterns, the company eliminated the fraud within six months. Alerts triggered when vendor bank details changed, and payment approvals were halted pending verification—saving the company significant funds and restoring vendor trust.
8. The Future of Fraud Protection
AI & Predictive Analytics
More services are leveraging deep-learning to anticipate fraud patterns rather than just react.
Blockchain & Distributed Ledger
Especially in supply chain and insurance, blockchain can provide immutable audit trails to reduce fraud risk.
Increased Regulatory Scrutiny
As fraud evolves, regulators are pushing more robust obligations on businesses—fraud protection becomes not just a cost but a compliance requirement.
Ecosystem Collaboration
Sharing fraud intelligence across organizations and industries will accelerate detection and prevention of sophisticated networks of fraudsters.
9. Final Thoughts
In today’s digital era, investing in fraud protection services is not optional—it’s a strategic imperative. From real-time transaction monitoring to vendor risk mitigation and machine learning-powered analytics, these services form a critical layer of defense against both external and internal fraud.
For IT managers, cybersecurity leaders and CEOs, the message is clear: assess your fraud exposure, select a service aligned with your risk profile, integrate it fully into your operations, and maintain continuous vigilance.
If you’re looking to bolster your fraud defenses, integrate them with comprehensive endpoint security and threat detection workflows for true resilience. Register for a demo with Xcitium’s OpenEDR today and discover how to combine fraud protection with advanced cybersecurity controls.
FAQ Section
Q1: What exactly do fraud protection services cover?
A: They cover identification, prevention and response to fraudulent activities—including payments, vendor transactions, identity theft and supply-chain issues.
Q2: Are fraud protection services only for financial institutions?
A: No. While finance is a major user, any organization—e-commerce, manufacturing, healthcare, education—can benefit from fraud protection.
Q3: How do I measure the ROI of fraud protection?
A: Compare the cost of service vs. estimated fraud losses prevented, reputational risk mitigated, operational efficiency gained. Use metrics such as chargeback reduction, vendor payment exception rates.
Q4: Can fraud protection services replace my cybersecurity team?
A: No. They complement cybersecurity and risk teams but don’t replace them. You still need threat detection, endpoint security, incident response and governance.
Q5: How do services handle privacy and compliance?
A: Leading providers ensure data encryption, comply with regulations like GDPR/PCI-DSS, maintain audit logs, and provide privacy-compliant monitoring frameworks.