Updated on October 28, 2025, by OpenEDR
Did you know that over 2,200 cyberattacks occur every single day—that’s one every 39 seconds? In this digital battleground, having a robust firewall for cyber security isn’t optional — it’s essential.
A firewall acts as your network’s gatekeeper, controlling what enters and exits your digital environment. Whether you’re managing a small business network or a large enterprise system, the right firewall can mean the difference between safety and catastrophe.
In this guide, we’ll break down what a firewall is, how it works, the different types available, and why it’s still one of the most vital tools in modern cybersecurity strategies.
What Is a Firewall in Cyber Security?
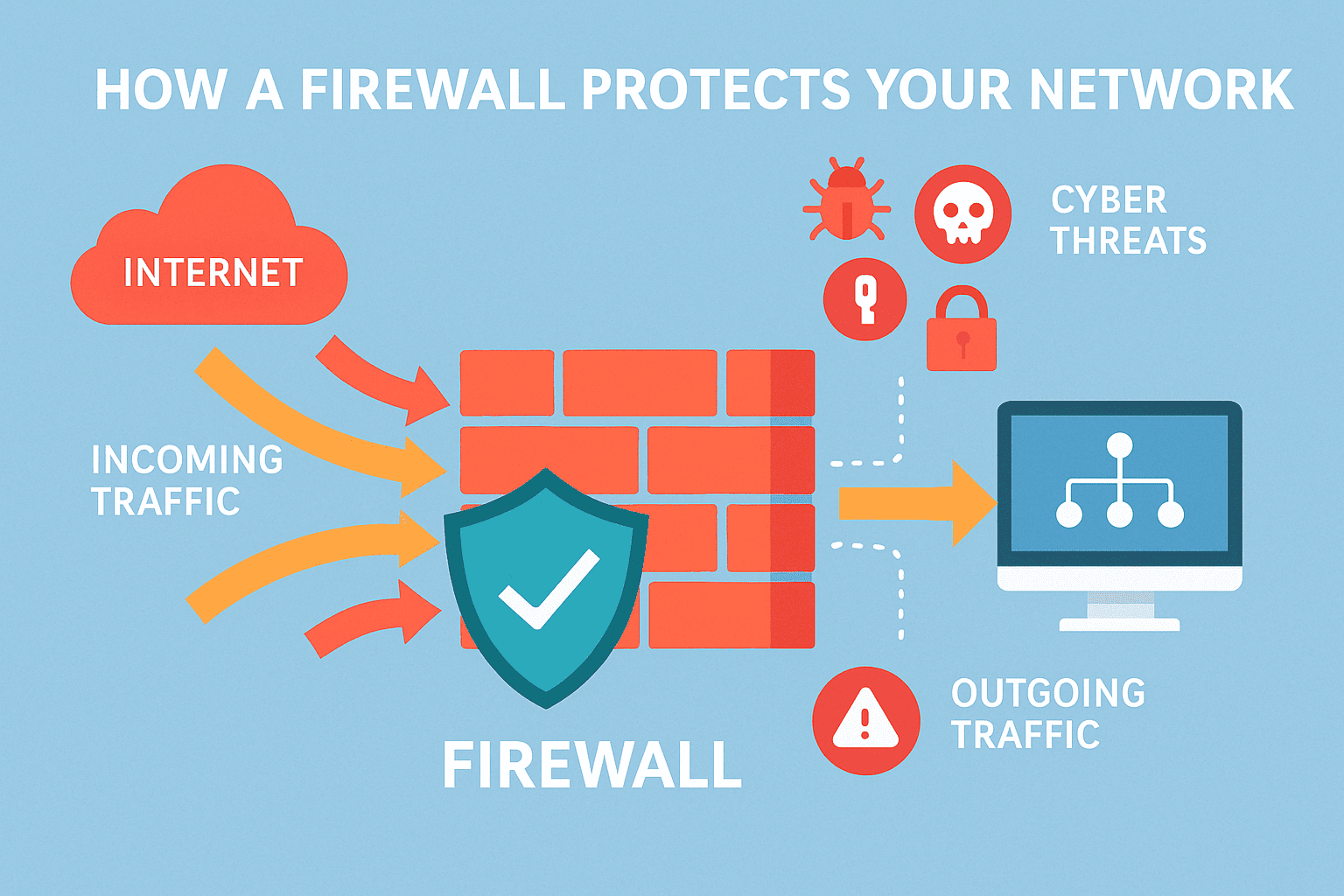
A firewall is a network security system that monitors and filters incoming and outgoing network traffic based on pre-defined security rules. In simpler terms, it acts as a barrier between your trusted internal network and untrusted external networks such as the internet.
Think of it like a security guard — inspecting every piece of data trying to enter or leave your network and allowing or blocking it depending on safety protocols.
Firewalls have evolved significantly since their invention in the late 1980s. Modern solutions now include Next-Generation Firewalls (NGFWs) equipped with AI, deep packet inspection (DPI), and intrusion prevention systems (IPS) for advanced threat detection.
How Firewalls Work: The Core Mechanism
Firewalls work by establishing a set of rules that define what kind of data packets are allowed to pass through your network.
Here’s a simplified process of how they function:
Data Request: A user sends or receives a data packet through the network.
Inspection: The firewall examines this packet — checking its source, destination, and protocol.
Filtering: It compares the packet against security policies (firewall rules).
Decision: The packet is either allowed through or blocked.
The Two Main Filtering Techniques:
Packet Filtering: Basic inspection of data packets based on IP address, port, or protocol.
Stateful Inspection: Monitors active connections and makes dynamic decisions based on the context of network traffic.
Modern firewalls combine these with deep packet inspection, AI-based anomaly detection, and application-level control for greater precision.
Importance of Firewalls in Cyber Security
Firewalls are foundational to every cybersecurity strategy. They:
Prevent Unauthorized Access: Stop hackers and malicious programs from entering private networks.
Filter Malicious Traffic: Identify and block data packets carrying malware or suspicious payloads.
Protect Against Data Breaches: Firewalls can prevent data exfiltration attempts from compromised devices.
Regulate Network Usage: Define which websites, applications, or devices can connect to your systems.
Support Compliance: Help meet regulations like GDPR, HIPAA, or PCI-DSS by enforcing network security policies.
Without a firewall, your network would be exposed like a house without a front door — wide open for intruders.
Types of Firewalls
Different environments require different firewall architectures. Here are the main types of firewalls used in cybersecurity today:
1. Packet-Filtering Firewalls
These are the most basic firewalls, examining each data packet and allowing or blocking it based on rules.
✅ Pros: Fast and efficient.
❌ Cons: Limited visibility into data content.
2. Proxy Firewalls (Application-Level Gateways)
Proxy firewalls act as intermediaries between users and external servers. They inspect traffic at the application layer (e.g., HTTP, FTP).
✅ Pros: Deep inspection of data packets.
❌ Cons: Can slow down network performance.
3. Stateful Inspection Firewalls
These track active network connections and make decisions based on both rules and context.
✅ Pros: More secure than basic packet filtering.
❌ Cons: May consume more system resources.
4. Next-Generation Firewalls (NGFWs)
NGFWs combine traditional firewall functions with advanced threat intelligence, deep packet inspection, and application awareness.
✅ Pros: Detects modern threats like ransomware and zero-day attacks.
❌ Cons: Higher cost and complexity.
5. Cloud-Based Firewalls (Firewall-as-a-Service)
These operate in the cloud, protecting distributed environments and remote users.
✅ Pros: Scalable and ideal for hybrid workforces.
❌ Cons: Requires strong internet connectivity.
Hardware vs. Software Firewalls
Hardware Firewalls
These are physical devices placed between your network and the gateway (router).
Ideal for large organizations.
Offers robust protection against external attacks.
Can be costly and require maintenance.
Software Firewalls
Installed directly on individual devices (computers, servers, etc.).
Provides internal network security.
Easy to deploy and manage.
Best for small businesses and personal use.
Hybrid Approach
Most modern companies use a combination of both for layered defense — hardware firewalls for perimeter protection and software firewalls for endpoint control.
Firewall Deployment in Cybersecurity Architecture
Firewalls form a key layer in the Defense-in-Depth (DiD) approach. Here’s how they fit within enterprise cybersecurity:
Perimeter Defense: Protects against external intrusions at the network edge.
Internal Segmentation: Creates secure zones within internal networks to prevent lateral movement of malware.
Endpoint Protection: Software firewalls safeguard individual devices.
Cloud Security Integration: Ensures protection extends to cloud apps and remote users.
When configured properly, firewalls can isolate attacks, limit damage, and enable visibility into network traffic — all crucial for Security Operations Centers (SOCs).
Firewall and Cyber Threat Protection
Firewalls are instrumental in blocking various cyber threats, including:
Malware & Ransomware Attacks
Phishing & Spoofing Attempts
DDoS (Distributed Denial of Service)
Unauthorized Remote Access
Insider Threats
Real-World Example
In 2021, a global manufacturing firm prevented a $5 million ransomware attack by using an NGFW configured to detect unusual outbound traffic patterns — stopping data exfiltration before encryption began.
The Role of Firewalls in a SOC (Security Operations Center)
In a Security Operations Center (SOC), firewalls are constantly monitored for alerts and anomalies. They:
Feed logs into SIEM tools (Security Information and Event Management).
Trigger real-time alerts for suspicious activity.
Support incident response workflows.
Combined with tools like Xcitium OpenEDR, SOC teams can automatically detect, isolate, and neutralize threats from compromised endpoints before they spread across the network.
Best Practices for Firewall Management
Implementing a firewall isn’t enough — it needs regular updates and proper configuration. Follow these best practices:
🔧 1. Define Clear Security Policies
Establish who can access which applications, services, or networks.
🧱 2. Enable Logging and Monitoring
Monitor all inbound and outbound traffic to detect suspicious activity.
🔄 3. Regularly Update Firewall Rules
Remove outdated rules to reduce attack surfaces.
🧠 4. Train IT Staff
Ensure your security team understands firewall configurations and best practices.
☁️ 5. Integrate with Cloud Security Tools
As more organizations move to hybrid environments, use cloud-native firewalls for continuous protection.
🧩 6. Test Regularly
Perform penetration testing and vulnerability scans to ensure the firewall works as intended.
Future of Firewalls in Cyber Security
As cyber threats evolve, so do firewalls. The next wave includes:
AI-Powered Firewalls that use behavior analytics for predictive threat detection.
Zero Trust Firewalls enforcing “never trust, always verify” principles.
Cloud-Native Firewalls for SaaS and multi-cloud environments.
Integration with XDR (Extended Detection and Response) systems for unified defense.
The firewall of tomorrow will not just block traffic — it will learn, adapt, and respond intelligently.
Benefits of Using a Firewall for Cyber Security
| Benefit | Description |
|---|---|
| Network Protection | Blocks malicious and unauthorized traffic. |
| Improved Performance | Filters unnecessary data, optimizing bandwidth. |
| Enhanced Visibility | Provides insights into network behavior. |
| Data Security | Prevents sensitive data leaks. |
| Compliance Support | Aids in meeting industry regulations. |
| Threat Detection | Identifies patterns of potential attacks. |
Why Businesses Need Firewalls in 2025
In 2025, cyber threats have become more sophisticated, with attacks like AI-driven phishing, deepfake ransomware, and insider sabotage.
A robust firewall for cyber security offers the first layer of automated protection against such advanced threats — blocking millions of intrusion attempts daily.
Without a firewall, your systems are vulnerable to:
Network infiltration
Data theft
Malware propagation
Regulatory penalties
Conclusion
A firewall for cyber security isn’t just another IT tool — it’s the foundation of digital safety. Whether you’re protecting a small office network or a multi-branch enterprise, firewalls remain essential for preventing intrusions, maintaining compliance, and securing data.
To build stronger defenses, combine traditional firewalls with next-gen EDR and cloud protection tools like Xcitium OpenEDR. Together, they provide real-time visibility, control, and prevention against evolving threats.
FAQs on Firewalls for Cyber Security
1. What is the main purpose of a firewall?
A firewall monitors and controls network traffic to prevent unauthorized access and protect systems from cyber threats.
2. How does a firewall protect against hackers?
It filters network packets, blocking suspicious or malicious connections before they can exploit vulnerabilities.
3. Are firewalls still necessary in 2025?
Yes — even with advanced AI and cloud tools, firewalls remain a vital first line of defense.
4. What’s the difference between a firewall and antivirus?
A firewall controls network traffic, while antivirus scans and removes malicious files. Together, they form layered protection.
5. What is the best type of firewall for businesses?
Next-Generation Firewalls (NGFWs) are ideal for enterprises, offering AI-based threat detection, VPN integration, and cloud support.