Updated on October 13, 2025, by OpenEDR
When devices communicate on a network, how do they know where to send data? That’s where the Address Resolution Protocol (ARP) comes in. Without ARP, your laptop wouldn’t find your printer, and your server wouldn’t communicate with the router. It’s a silent but essential player in daily operations.
Introduction: Why ARP Still Matters in Modern Networks
But here’s the problem: ARP was designed decades ago—long before cybersecurity became a major concern. Attackers often exploit ARP through techniques like ARP spoofing to intercept sensitive data. According to IBM’s threat research, man-in-the-middle (MITM) attacks exploiting ARP manipulation remain a top vector for network breaches.
This article explores what ARP is, how it works, its benefits, risks, and the steps enterprises can take to secure it.
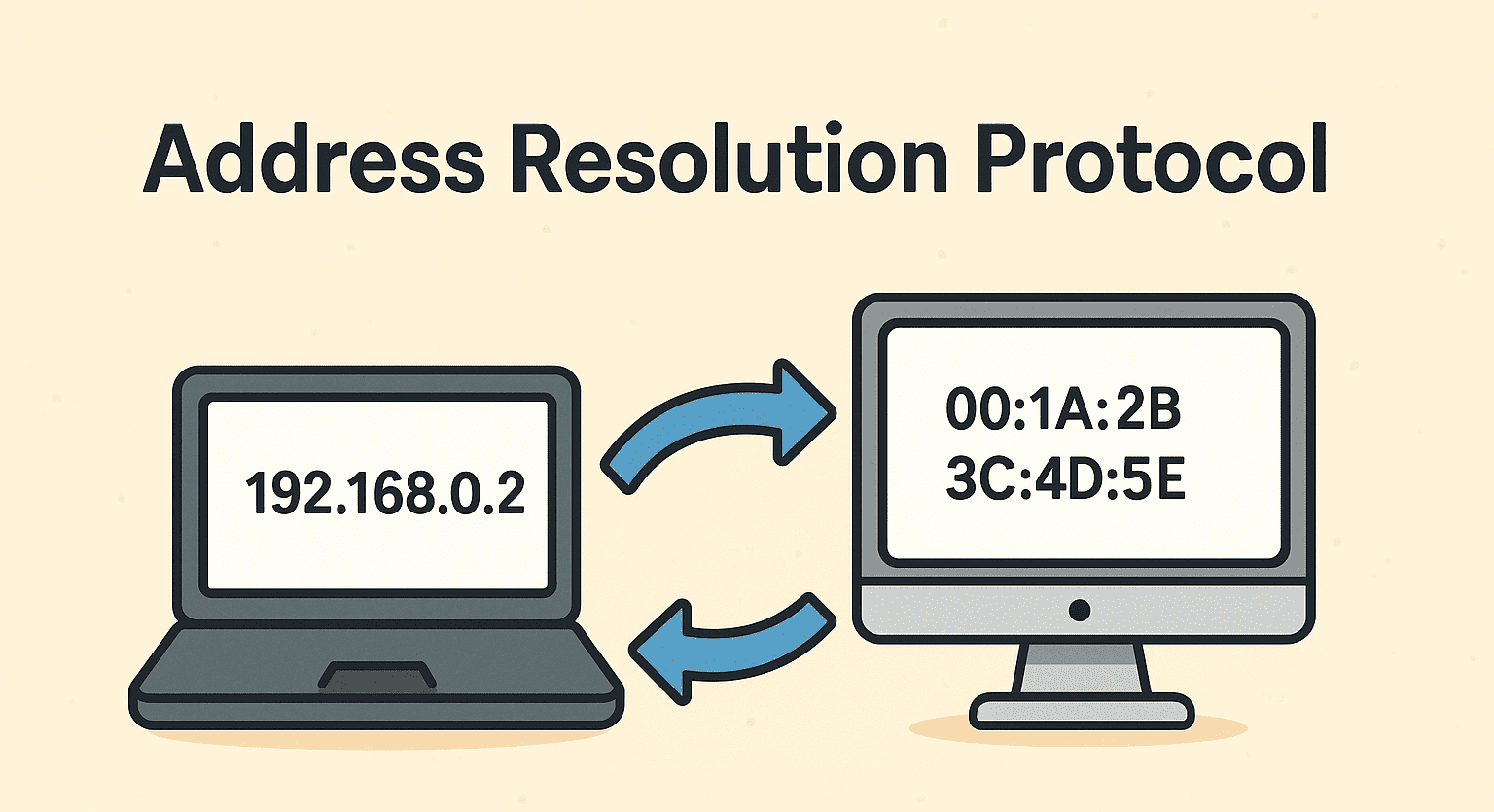
1. What Is Address Resolution Protocol (ARP)?
The Address Resolution Protocol (ARP) is a communication protocol used to map an IP address (logical address) to a device’s MAC address (physical hardware address) on a local area network (LAN).
Why ARP Is Important:
Every device has both an IP address and a MAC address.
ARP ensures packets are delivered to the right device on a LAN.
It acts as a translator between logical and physical addresses.
👉 In simple terms, ARP is like a phonebook that helps devices find each other on a network.
2. How ARP Works Step by Step
When a device wants to communicate with another device in a network, it follows this process:
Device Sends ARP Request: “Who owns IP address X?”
Broadcast: This request goes to all devices on the LAN.
Device with Matching IP Responds: “That’s me! My MAC address is Y.”
Communication Begins: The sender stores the IP-MAC pair in its ARP cache for faster future communication.
Example:
Your computer wants to connect to a printer at
192.168.1.15.It broadcasts an ARP request.
The printer responds with its MAC address.
Data packets are then sent directly to the printer.
👉 This process happens in milliseconds, every time you access a local device.
3. Types of ARP
Different variations of ARP exist to support modern networking needs:
Proxy ARP: A router responds on behalf of another device.
Gratuitous ARP: A device announces its presence without being asked (often for redundancy).
Inverse ARP (InARP): Maps a known MAC address to an IP.
Reverse ARP (RARP): Outdated; assigns IP addresses to devices.
👉 These variations ensure ARP works in different environments—from simple LANs to enterprise-grade networks.
4. Benefits of Address Resolution Protocol
Despite its age, ARP continues to provide critical networking advantages:
✅ Seamless Communication: Devices find each other automatically.
✅ Low Latency: Fast address mapping for real-time applications.
✅ Simplicity: Works in the background without user input.
✅ Compatibility: Supports IPv4 networks globally.
✅ Efficiency: Uses ARP cache to reduce repeated requests.
👉 ARP makes networks efficient, self-learning, and user-friendly.
5. Security Risks of ARP
Here’s the catch: ARP wasn’t designed with modern cybersecurity in mind.
Key Threats:
ARP Spoofing / Poisoning: Hackers send fake ARP responses to redirect traffic.
Man-in-the-Middle Attacks (MITM): Attackers intercept data between two devices.
Denial of Service (DoS): Malicious ARP messages flood and crash networks.
Data Theft: Sensitive data like credentials or payment info can be captured.
👉 These risks make ARP a weak link in enterprise network security.
6. How to Protect Against ARP Attacks
Enterprises must adopt proactive ARP security measures:
🔒 Static ARP Entries: Assign fixed IP-MAC pairs for critical devices.
🔒 ARP Inspection (DAI): Validates ARP packets before they’re processed.
🔒 VLAN Segmentation: Limits the impact of ARP spoofing within isolated networks.
🔒 Encryption: Use VPNs or TLS to protect data even if intercepted.
🔒 Monitoring Tools: IDS/IPS solutions detect unusual ARP traffic.
👉 Combined, these strategies minimize ARP exploitation risks.
7. ARP in Enterprise Networking
ARP is essential in every business environment:
Data Centers: Facilitates communication between thousands of servers.
Corporate Offices: Ensures seamless connectivity for devices and printers.
Financial Systems: Keeps trading and banking systems online.
Healthcare: Connects devices handling sensitive patient data.
👉 No matter the industry, ARP underpins daily operations and security strategies.
8. Future of Address Resolution Protocol
Even as technology evolves, ARP continues to adapt:
IPv6 Replacement: Uses Neighbor Discovery Protocol (NDP) instead of ARP.
AI-Driven Monitoring: Machine learning detects abnormal ARP traffic.
Integration with Zero Trust: Adds device verification for enhanced security.
Next-Gen Firewalls: Offer ARP spoofing prevention natively.
👉 ARP isn’t going away—it’s evolving alongside cybersecurity.
Quick Recap: What Is Address Resolution Protocol
✅ ARP maps IP addresses to MAC addresses.
✅ Works silently in the background of every LAN.
✅ Critical for seamless device communication.
✅ Vulnerable to spoofing and MITM attacks.
✅ Enterprises must secure ARP with modern tools.
FAQs on Address Resolution Protocol
1. What is Address Resolution Protocol in simple terms?
It’s the system that links a device’s IP address to its physical MAC address.
2. Why is ARP important?
Without ARP, devices wouldn’t know how to send data to each other on a local network.
3. Is ARP secure?
By default, no. It’s vulnerable to spoofing but can be protected with tools like DAI and VLANs.
4. What is ARP spoofing?
It’s when attackers send fake ARP messages to intercept or redirect network traffic.
5. What replaces ARP in IPv6?
The Neighbor Discovery Protocol (NDP) takes ARP’s role in IPv6 networks.
Final Thoughts
So, what is Address Resolution Protocol (ARP)? It’s the invisible but vital translator that makes modern networking possible. While ARP ensures smooth communication between devices, it also presents risks if left unprotected.
For IT leaders, the takeaway is clear: securing ARP is just as important as securing endpoints, firewalls, and applications.
🚀 Ready to strengthen your enterprise defenses against ARP spoofing and network attacks?
Request a demo from Xcitium’s OpenEDR today and discover how advanced endpoint detection and response (EDR) protects your infrastructure.