Updated on February 2, 2026, by OpenEDR
Cyber threats are no longer a distant risk—they are a daily reality for organizations of every size. From ransomware and phishing to insider threats and supply chain attacks, modern businesses face relentless pressure to secure their digital assets. This is why enterprise cybersecurity solutions have become a strategic necessity, not just an IT investment.
Enterprise cybersecurity solutions go beyond basic protection. They provide visibility, automation, and control across complex environments. For IT managers, cybersecurity professionals, and executives, understanding how these solutions work is essential to protecting operations, reputation, and revenue.
In this guide, we’ll explore what enterprise cybersecurity solutions are, why they matter, and how to choose the right approach for your organization.
What Are Enterprise Cybersecurity Solutions?
Enterprise cybersecurity solutions are integrated security technologies and frameworks designed to protect large, complex IT environments. These solutions secure endpoints, networks, cloud infrastructure, users, and data—often from a single, centralized platform.
In simple terms:
Enterprise cybersecurity solutions protect organizations by preventing, detecting, and responding to cyber threats at scale.
Unlike consumer-grade tools, enterprise solutions are built for:
Large user bases
Distributed networks
Hybrid and cloud environments
Regulatory and compliance requirements
Why Enterprise Cybersecurity Solutions Are Critical Today
The attack surface has expanded rapidly. Cloud adoption, remote work, and third-party integrations have created new vulnerabilities that traditional security tools cannot manage alone.
Key Drivers for Enterprise Security Adoption
Rising ransomware and data breach costs
Sophisticated, targeted cyberattacks
Regulatory pressure and compliance mandates
Increased reliance on cloud and SaaS platforms
Shortage of skilled cybersecurity professionals
Enterprise cybersecurity solutions help organizations stay resilient in this evolving threat landscape.
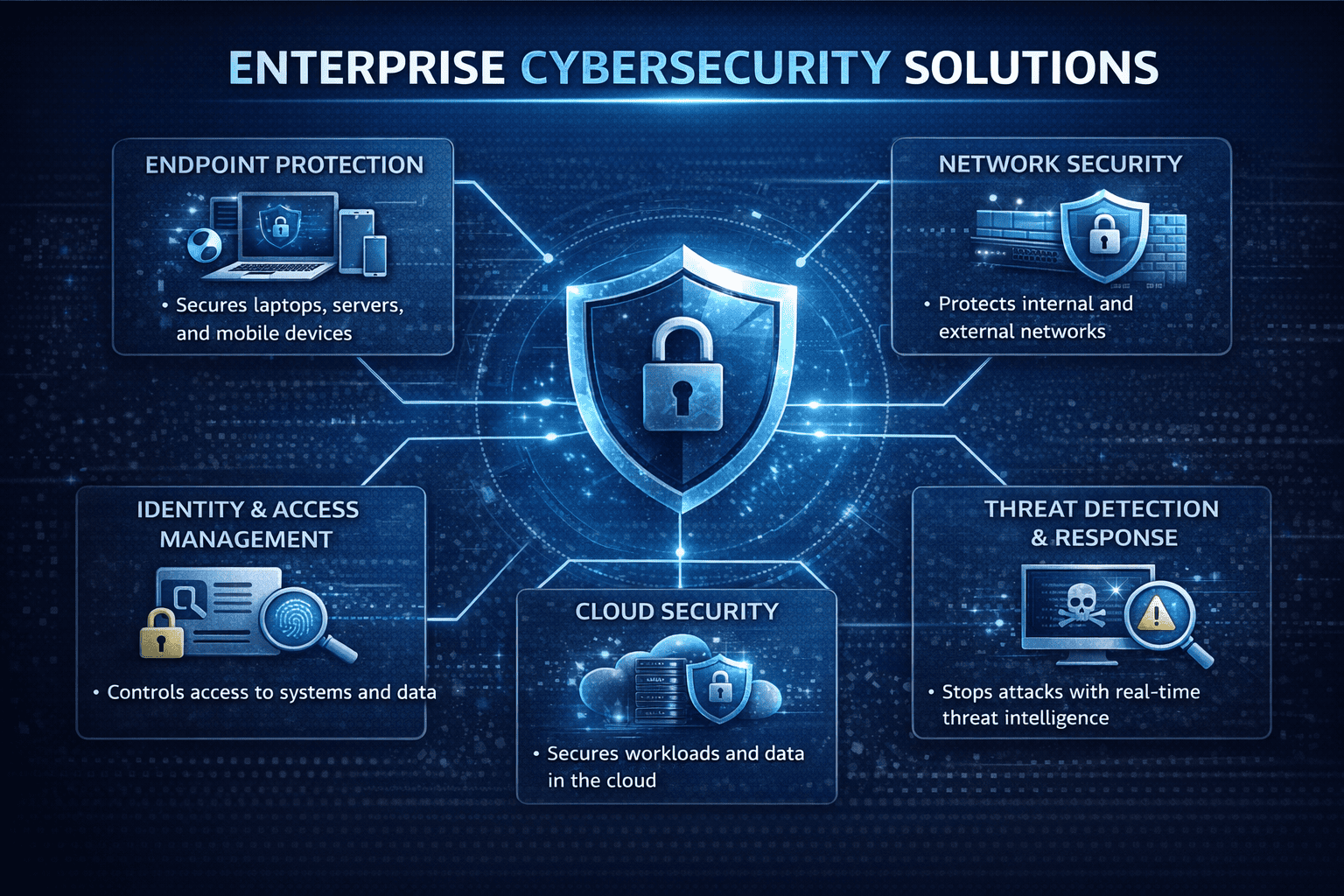
Core Components of Enterprise Cybersecurity Solutions
To understand how enterprise cybersecurity solutions work, it’s important to break them into key components.
1. Endpoint Protection
Secures laptops, servers, and mobile devices against malware, ransomware, and exploits.
2. Network Security
Protects internal and external traffic using firewalls, intrusion detection, and segmentation.
3. Identity and Access Management (IAM)
Controls who can access systems, data, and applications.
4. Cloud Security
Secures workloads, storage, and applications in cloud environments.
5. Threat Detection and Response
Uses analytics and automation to identify and contain threats in real time.
Together, these layers form a comprehensive enterprise defense strategy.
Enterprise Cybersecurity Solutions vs Traditional Security Tools
Many organizations still rely on fragmented tools that were never designed for enterprise-scale threats.
| Feature | Traditional Tools | Enterprise Cybersecurity Solutions |
|---|---|---|
| Scalability | Limited | Enterprise-grade |
| Visibility | Siloed | Centralized |
| Automation | Minimal | Advanced |
| Threat Response | Reactive | Proactive |
| Cloud Readiness | Low | High |
Enterprise cybersecurity solutions unify security operations and reduce complexity.
How Enterprise Cybersecurity Solutions Reduce Business Risk
Cybersecurity is no longer just a technical concern—it’s a business risk issue.
Business Benefits Include:
Reduced downtime and disruption
Lower breach recovery costs
Improved regulatory compliance
Stronger customer trust
Better executive-level reporting
For CEOs and founders, enterprise cybersecurity solutions support long-term business continuity and growth.
The Role of Automation and Zero Trust
Modern enterprise environments generate more alerts than human teams can handle manually.
Automation Advantages
Faster threat containment
Reduced alert fatigue
Consistent response actions
Lower operational costs
Zero Trust Security
Enterprise cybersecurity solutions increasingly follow a Zero Trust model:
Never trust by default
Always verify users and devices
Continuously assess risk
This approach limits lateral movement even after a breach.
Common Challenges When Implementing Enterprise Cybersecurity Solutions
While powerful, enterprise security platforms are not without challenges.
Common Issues
Tool sprawl and complexity
Integration difficulties
Lack of skilled personnel
Budget constraints
Resistance to process change
Choosing the right platform and strategy helps overcome these obstacles.
How to Choose the Right Enterprise Cybersecurity Solution
Selecting enterprise cybersecurity solutions requires alignment between security goals and business needs.
Key Evaluation Criteria
Coverage across endpoints, cloud, and network
Built-in automation and response
Centralized visibility and reporting
Ease of deployment and management
Vendor transparency and support
A unified platform often delivers better outcomes than multiple disconnected tools.
Best Practices for IT Managers and Security Teams
To maximize the value of enterprise cybersecurity solutions, organizations should:
Standardize security policies across environments
Monitor threats continuously, not periodically
Regularly test incident response plans
Align security metrics with business goals
Train users to recognize social engineering attacks
Security is most effective when technology and people work together.
Industry-Specific Use Cases for Enterprise Cybersecurity Solutions
Different industries face different threat profiles.
Financial Services
Protect sensitive financial data
Prevent fraud and account takeover
Healthcare
Secure patient data
Meet HIPAA and privacy requirements
Technology and SaaS
Protect intellectual property
Secure cloud-native environments
Manufacturing
Defend against operational disruption
Secure industrial control systems
Enterprise cybersecurity solutions adapt to each industry’s risk landscape.
Actionable Tips for Executives
Treat cybersecurity as a board-level issue
Demand clear security metrics and reporting
Invest in prevention, not just detection
Prioritize automation to offset staffing shortages
Align cybersecurity strategy with business growth plans
Understanding enterprise cybersecurity solutions helps leadership make informed decisions.
FAQ: Enterprise Cybersecurity Solutions
1. What are enterprise cybersecurity solutions?
They are integrated security platforms designed to protect large organizations from advanced cyber threats.
2. How do enterprise cybersecurity solutions differ from antivirus software?
They provide multi-layered protection, automation, and visibility across the entire organization.
3. Are enterprise cybersecurity solutions only for large companies?
No. Mid-sized organizations also benefit as they scale and face more complex threats.
4. Do enterprise cybersecurity solutions support cloud environments?
Yes. Modern solutions are built to secure hybrid and cloud-first infrastructures.
5. How long does it take to deploy enterprise cybersecurity solutions?
Deployment time varies but can range from days to weeks depending on scope and complexity.
Why Enterprise Cybersecurity Solutions Are a Strategic Investment
Cybersecurity is no longer optional—it’s foundational. Organizations that adopt modern enterprise cybersecurity solutions gain stronger defenses, clearer visibility, and faster response capabilities. In today’s threat landscape, resilience is built through proactive, automated, and unified security.
For IT leaders and executives, investing in the right enterprise cybersecurity solutions is an investment in trust, stability, and long-term success.
Ready to Strengthen Your Enterprise Security Strategy?
Take the next step toward proactive, automated, and scalable protection.
👉 Register now:
https://openedr.platform.xcitium.com/register/
Discover how modern enterprise cybersecurity solutions can help your organization stay ahead of today’s threats.