Updated on January 30, 2026, by OpenEDR
Cyberattacks aren’t slowing down—and neither can your security team. With alert fatigue, limited resources, and increasingly sophisticated threats, traditional security operations simply can’t keep up. This is where SOAR cyber security steps in.
If your SOC is overwhelmed by alerts, manual investigations, or delayed responses, you’re not alone. Organizations across industries are turning to SOAR cyber security to automate, orchestrate, and accelerate incident response—without sacrificing accuracy or control.
In this guide, we’ll break down what SOAR cyber security is, why it matters, how it works, and how your organization can use it to stay ahead of modern cyber threats.
What Is SOAR Cyber Security?
SOAR cyber security stands for Security Orchestration, Automation, and Response. It’s a technology framework that helps organizations streamline security operations by connecting tools, automating workflows, and responding to incidents faster.
At its core, SOAR cyber security combines three essential capabilities:
Orchestration: Integrates multiple security tools into a unified system
Automation: Reduces manual tasks using predefined workflows
Response: Enables faster, more consistent incident handling
Instead of analysts jumping between dashboards and tools, SOAR cyber security centralizes everything into one coordinated response platform.
Why SOAR Cyber Security Is No Longer Optional
Cybersecurity teams face a harsh reality: more alerts, fewer resources, and higher expectations. SOAR cyber security addresses these challenges head-on.
Key Challenges Without SOAR
Alert overload causing analyst burnout
Slower incident response times
Inconsistent handling of threats
Higher risk of human error
How SOAR Cyber Security Solves Them
Automates repetitive investigations
Prioritizes alerts based on risk
Standardizes response playbooks
Reduces Mean Time to Detect (MTTD) and Respond (MTTR)
For IT managers and executives, SOAR cyber security isn’t just a technical upgrade—it’s a business enabler.
Core Components of SOAR Cyber Security
Understanding the building blocks of SOAR cyber security helps you see how it fits into your existing security stack.
1. Security Orchestration
SOAR cyber security connects tools like SIEMs, EDRs, firewalls, threat intelligence feeds, and ticketing systems. This orchestration eliminates silos and improves visibility.
2. Security Automation
Automation handles repetitive tasks such as:
IP reputation checks
Malware sandboxing
User account suspension
Log enrichment
This frees analysts to focus on complex decision-making.
3. Incident Response Management
SOAR cyber security uses playbooks to ensure incidents are handled consistently, even across large teams or multiple locations.
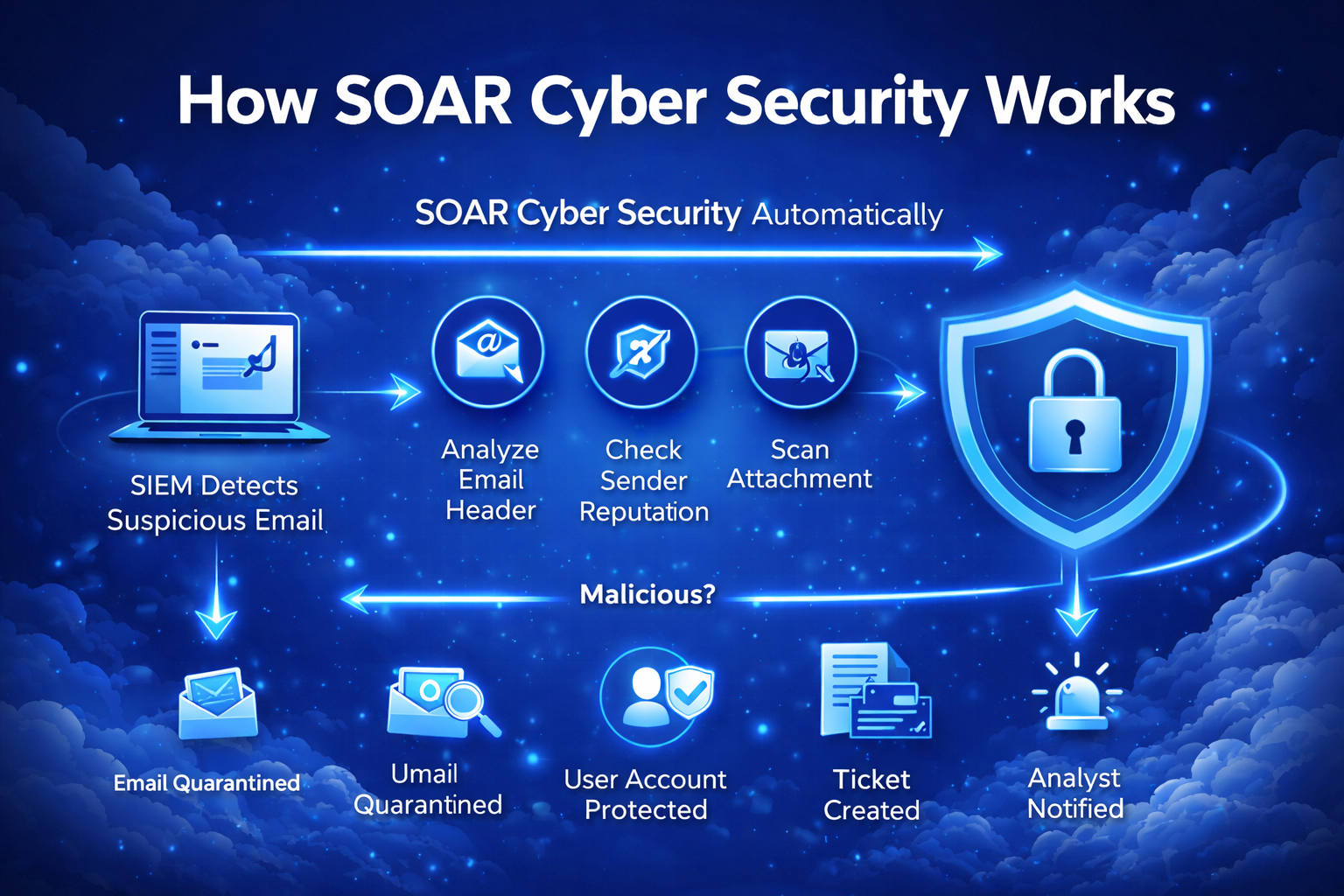
How SOAR Cyber Security Works in Real Life
Let’s look at a simple example.
Scenario: Phishing Email Detected
SIEM detects suspicious email
SOAR cyber security automatically:
Analyzes email headers
Checks sender reputation
Scans attachments
If malicious:
Email is quarantined
User account is protected
Ticket is created
Analyst is notified
All of this happens in seconds—not hours.
Key Benefits of SOAR Cyber Security
1. Faster Threat Response
Automation significantly reduces response time, minimizing damage.
2. Reduced Analyst Burnout
SOAR cyber security eliminates repetitive tasks, improving morale and efficiency.
3. Improved Security Accuracy
Standardized playbooks reduce errors and ensure compliance.
4. Better ROI on Security Tools
You maximize existing investments by orchestrating them effectively.
5. Executive-Level Visibility
Dashboards and reports help leadership understand security performance.
SOAR Cyber Security vs SIEM: What’s the Difference?
While often used together, SOAR cyber security and SIEM serve different purposes.
| Feature | SIEM | SOAR Cyber Security |
|---|---|---|
| Log Collection | ✅ | ❌ |
| Threat Detection | ✅ | ❌ |
| Automated Response | ❌ | ✅ |
| Workflow Automation | ❌ | ✅ |
| Tool Orchestration | ❌ | ✅ |
Best practice: Use SIEM for detection and SOAR cyber security for response.
Industries That Benefit Most from SOAR Cyber Security
SOAR cyber security is valuable across sectors, especially those with high regulatory or threat exposure.
Industries Seeing the Biggest Impact
Financial Services
Healthcare
Manufacturing
Retail & eCommerce
SaaS & Cloud Providers
Government & Critical Infrastructure
For CEOs and founders, SOAR cyber security supports growth without scaling security headcount.
How to Successfully Implement SOAR Cyber Security
A thoughtful rollout ensures long-term success.
Step 1: Identify Repetitive Tasks
Start with high-volume, low-complexity incidents.
Step 2: Build Playbooks
Create clear workflows aligned with your security policies.
Step 3: Integrate Existing Tools
Connect SIEM, EDR, threat intelligence, and ticketing systems.
Step 4: Start Small, Then Scale
Pilot a few use cases before expanding.
Step 5: Measure and Optimize
Track KPIs like MTTR, alert volume, and analyst productivity.
Common Mistakes to Avoid with SOAR Cyber Security
Even powerful platforms can fail without proper planning.
Automating without understanding workflows
Ignoring analyst feedback
Over-engineering playbooks
Lack of executive buy-in
Successful SOAR cyber security balances automation with human oversight.
The Future of SOAR Cyber Security
As threats evolve, SOAR cyber security continues to mature.
Emerging Trends
AI-driven decision-making
Cloud-native SOAR platforms
Deeper threat intelligence integration
Autonomous response capabilities
Organizations that adopt SOAR cyber security early gain a lasting competitive advantage.
Actionable Tips to Maximize SOAR Cyber Security Value
Automate first-level triage
Align playbooks with compliance requirements
Regularly update workflows
Train analysts on SOAR usage
Review metrics monthly
These best practices ensure your SOAR cyber security investment delivers measurable results.
Frequently Asked Questions (FAQ)
1. What does SOAR cyber security stand for?
SOAR cyber security stands for Security Orchestration, Automation, and Response, focusing on faster and smarter incident handling.
2. Is SOAR cyber security suitable for small businesses?
Yes. Many modern SOAR cyber security platforms scale for SMBs and MSSPs.
3. Does SOAR replace security analysts?
No. SOAR cyber security enhances analysts by removing repetitive tasks, not replacing human judgment.
4. How long does it take to implement SOAR cyber security?
Initial deployments can take weeks, with ongoing optimization over time.
5. Can SOAR cyber security integrate with existing tools?
Absolutely. Integration is a core feature of SOAR cyber security platforms.
Final Thoughts: Why SOAR Cyber Security Is a Game-Changer
Cyber threats are relentless, but your response doesn’t have to be reactive. SOAR cyber security empowers organizations to respond faster, smarter, and more consistently—without overwhelming their teams.
If you’re serious about improving your security posture, reducing risk, and scaling operations efficiently, now is the time to adopt SOAR cyber security.
Ready to Strengthen Your Cyber Defense?
Take the next step toward automated, intelligent security operations.
👉 Register now and experience next-generation cyber defense:
https://openedr.platform.xcitium.com/register/