What are Endpoint Detection and Response EDR Tools?
Updated on April 7, 2023, by OpenEDR
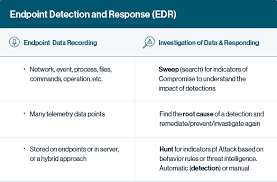
Why is EDR Important?
Endpoint Detection and Response EDR Tools activity allows security teams to eliminate threats quickly and minimize the impact of an attack. It is one of the essential parts of the EPP. Providing insight into EDR security capabilities, this article focuses on the endpoint security market. From tools to features and scopes, you will get everything here in this article.
What are Endpoint Detection and Response EDR Tools? – How to Choose an EDR?
EDR is one of the most valuable terms referred to as a solution that records behavior on endpoints, detects suspicious behavioral patterns using data analytics and context-based information, blocks threats, and enables security reviewers to remediate and fix compromised systems.
To achieve the targets, multiple tools are available that can detect endpoint threats and help the security team investigate. Endpoint detection tools are a prominent element of a current endpoint security strategy because they are the most valuable means of witnessing intrusions.

What are Endpoint Detection and Response EDR Tools?- What are the EDR tools?
EDR tools alert security teams of malicious activity and enable immediate investigation and containment of attacks on endpoints. EDR solutions aggregate data on endpoints, including process execution, endpoint communication, and user logins; analyze data to discover anomalies and malicious activity; and record data about malicious activity enabling security teams to investigate and respond to incidents. These endpoints can be a laptop, workstation or laptop, server, cloud system, mobile, or IoT device. So, now you know what endpoint detection and response (EDR) tools are.
What are Endpoint Detection and Response EDR Tools and Practices?- How does EDR Work?
Data from endpoints, including applications running, authentication attempts, and more, is ingested by EDR solutions. Here we will guide you on how EDR works:
To analyze suspicious activity, EDR solutions analyze circumstances from desktops, mobile devices, laptops, and more. Following the same, they generate alerts that make the security team investigate the issues. The Endpoint Detection and Response tools available also accumulate telemetry data on dubious activity and may increase that information with other contextual data from correlated circumstances. It evolves and incorporates a broader set of features.
What are Endpoint Detection and Response EDR Tools?- What are the capabilities of Best EDR Software?
There are multiple features of EDR solutions, and here are some of them.
1. Simplify the investigations
When using security Endpoint Detection and Response tools to get a complete picture of malicious activity, ensure that you choose the one with reduced response time and investigate in detail. A tool can simplify the investigation process by automatically revealing the root cause, sequence of events, and threat intelligence details of alerts from any source.
2. Provides a broad look at the malicious activity
With the help of the EDR tool, you can look for the activity more comprehensively. The definitive explanations offer a comprehensive set of machine knowledge and analytics methods that catch advanced real-time hazards. Even you will get more accurate results.
3. Endpoint protection reduces your attack surface.
Aside from blocking attacks, endpoint security tools must prevent data loss and unauthorized access with features like host firewalls and device control.
4. It should be cloud-delivered security.
The Cloud-based management and deployment streamlines operations and even eliminates the burden of on-premises servers. Besides this, it quickly scales and handles more users and data.
5. Forensics
By offering forensic capabilities, EDR tools can identify threats and surface similar activities that may have been missed. It can even help establish timelines and identify affected systems before a breach occurs.
6. Automation
When you consider advanced Endpoint Detection and Response tools, you will notice intuitive remediate activities like automatically stopping or disconnecting compromised processes and alerting relevant parties about the same.
What are Endpoint Detection and Response EDR Tools?- Why is EDR essential for your business?
No matter how advanced your system is, cyberpunk somehow finds its way to get through your defenses. It increases the necessity for an endpoint security strategy. Here are some of the compelling reasons for the same.
7. Prevention will not help protection.
You never know when you have to deal with the prevention fails in the organization. Because in case this happens, you will have nothing. Attackers can take this as an advantage to navigate inside your network.
8. There needs to be more visibility.
When the company finally finds the victim, they spend months remitting the incident and understanding what happened. It is because of a lack of visibility.
9. Adversaries can be inside your network and can return anytime
Cyberpunk often comes inside your network through their range of knowledge and even manages to return at will. The company could not be able even to identify the root cause.
10. Having complete data is one of many solutions.
When a company finds out about adversaries, the data is not the only solution they demand. Having the resources to analyze and take action against those activities is essential.
What are Endpoint Detection and Response EDR Tools?- What are the capabilities of EDR?
We have provided you with complete information about the EDR tools. Endpoint detection and response tools are essential to eliminate threat factors in the company.
Open EDR tools are one of the ideal choices to eliminate the threats your office might face. You visit their website to learn more about them openedr.com
FAQ Section