EDR Report
Updated on July 4, 2023, by OpenEDR
What is an EDR?
Are You Worried About Endpoint Security for Your Organization? With cyberattacks becoming ever more sophisticated, having an effective endpoint detection and response (EDR) solution in place has never been more critical – yet with so many products on the market available to businesses, it may seem daunting to decide on one suitable for them.
7 Key Features to Look for in an Effective Endpoint Detection and Response (EDR) Solution
In this blog post, we’ll outline seven features an EDR must possess so you can make an informed choice and protect against advanced threats for an enjoyable EDR experience! So sit back, relax, and let’s dive into this EDR report and solution together!
What is an EDR Report?
Endpoint Detection and Response (EDR report) is a cybersecurity solution designed to detect and respond to advanced threats targeting endpoints such as laptops, servers, or mobile devices – such as malware, ransomware, phishing attacks, or any other activity that compromises network security.
EDR serves to give real-time visibility of endpoint activities across your organization’s network, such as file changes, registry modifications, system events, and user behavior analysis in order to detect suspicious activities that could indicate security breaches or compromises.
EDR Report – EDR Key Elements of an Effective EDR Solution
An EDR report is crucial in protecting digital endpoints against cyber threats. Here are some features to look out for when searching for EDR:
Real-Time Monitoring: For maximum protection, an EDR solution must provide real-time monitoring across all endpoints, including servers, desktops, laptops, and mobile devices. This allows attackers to be detected as quickly as they occur and countered swiftly.
Behavior analysis: EDR solutions should include behavioral analytics capabilities to detect any anomalous or suspicious endpoint behavior patterns on endpoint devices and identify any anomalies or suspicious activity on them, thereby helping detect advanced persistent threats (APTs) which would otherwise go undetected by traditional security solutions.
Automated Response: An ideal EDR solution should include automated response capabilities that allow it to identify threats without human involvement and take immediate action against them, thus decreasing response times and mitigating damage caused by attacks.
Centralized Management: Your EDR solution must offer centralized management features that allow administrators to easily monitor all endpoints from a single interface, increasing visibility into endpoint activities across the organization and giving administrators greater oversight.
Integrations with Other Security Tools: Your EDR solution should seamlessly integrate with other security tools such as SIEM solutions, threat intelligence platforms, and firewalls to provide maximum protection from potential cyberattacks.
Maintaining Updates: Cybercriminals are constantly finding new ways to attack companies’ systems; therefore, your EDR tool must regularly update its signature database in order to effectively detect emerging threats.
Reporting Capabilities: Your EDR tool of choice must provide robust reporting features to provide insight into ongoing endpoint activities across your network infrastructure.
When selecting an EDR Solution for your business or organization, ensure it offers real-time monitoring capabilities, behavioral analysis capabilities, and automated response features – these should all be part of an ideal EDR report tool.
EDR Report – Benefits of Employing EDR Solutions
An effective Endpoint Detection and Response (EDR) solution offers many advantages for organizations of all sizes.
An EDR report can help security teams identify threats that traditional antivirus software fails to recognize, using behavioral analysis techniques to detect any unusual endpoint activity that allows them to quickly respond before any damage can be caused.
EDR solutions give organizations more insight into their endpoint environment by gathering detailed information about each device and activity within their environment, giving security teams greater insight into its overall security posture.
EDR solutions enable faster response times in case of cyber attacks or breaches, with automated incident response capabilities built-in that quickly contain threats and minimize damages.
EDR solutions help security teams stay ahead of any potential damage by providing real-time alerts of suspicious activities on endpoints, enabling them to take proactive measures before any damage can occur.
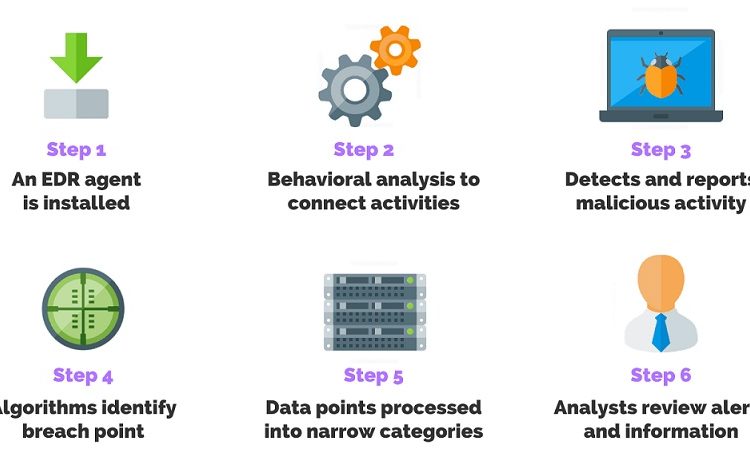
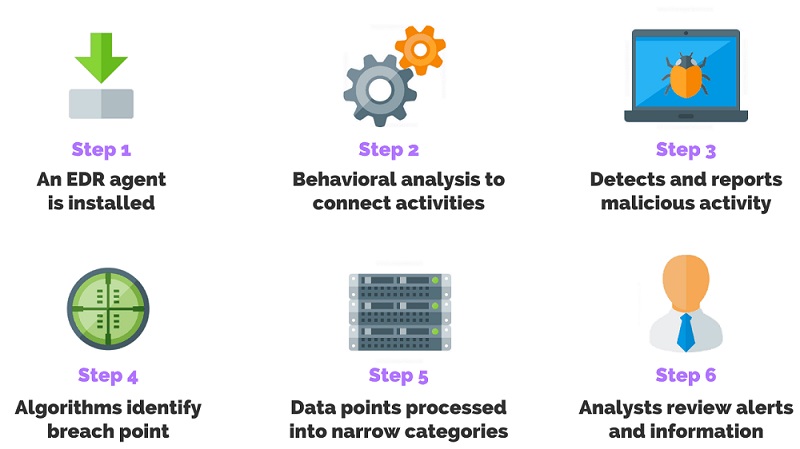
EDR Implementation
Implementation of EDR solutions facilitates compliance with industry regulations such as GDPR and HIPAA by ensuring all endpoints remain protected and monitored 24/7.
Employing an Endpoint Detection and Response (EDR) solution provides organizations with enhanced threat detection capabilities as well as increased visibility into their endpoint environment, leading to higher cybersecurity protection standards across industries regardless of size or scale.
Conclusion – EDR Report
As businesses adapt to an ever-evolving digital landscape, endpoint security becomes ever more essential. Implementing an Endpoint Detection and Response (EDR) solution can protect against cyber threats while streamlining IT operations – by prioritizing seven key features described here such as comprehensive visibility, threat intelligence integration, rapid response capabilities, automation/scalability/automation scalability/automation scalability capabilities/user behavior monitoring/advanced analytics capabilities/robust reporting; your EDR solution meets industry standards.
Employing an EDR report that prioritizes these attributes will not only bolster their cybersecurity measures but also unlock numerous other advantages, such as increased productivity and cost savings. With new threats constantly emerging on the digital battlefield, taking proactive measures to secure endpoints is absolutely critical to sustained enterprise growth and success. Take time now to review existing security systems or implement one if one hasn’t been done already – it could prove one of the wisest investments you ever make for the future of your business!
See Also:
EDR